What Is Phishing? – Definition, Types of Attacks, Examples 2025
In today’s digital world, phishing is a big threat to both people and companies. But what is phishing, and why should you worry about it? Let’s dive into the world of phishing and see how you can protect yourself and your online stuff.
Key Takeaways
- Phishing is a common cybercrime that uses tricks to steal sensitive info from people who aren’t careful.
- Phishing attacks can happen through emails, texts, or even phone calls, so you need to be alert.
- Knowing how phishers work can help you spot and avoid these dangerous tricks.
- Being careful and using strong anti-phishing tools is key to keeping safe from phishing attacks.
- Learning about the latest phishing tricks and how to fight them is important for better online safety.

Understanding Phishing: The Cyber Threat Lurking in Your Inbox
Phishing is a sneaky cyber threat that hides in emails and websites. It tricks people into sharing sensitive info or doing things that put their security at risk.
Read More: What is phishing in cyber security?
Phishing Definition: Dissecting the Malicious Act
Phishing is a type of social engineering. It uses tricks to make people give away important info. Scammers send fake emails or make fake websites that look like they’re from trusted places. They try to get people to share things like passwords or credit card numbers.
Read More: Exploring the Various Types of Cyber Security Threats
Phishing Techniques: How Attackers Bait Their Targets
Phishers use many ways to catch their victims. Here are some common methods:
- They send emails that look like they’re from trusted sources. These emails tell the person to click on a bad link or share private info right away.
- They make fake websites that look real. This makes users think they’re on a safe site and enter their login details.
- They use tricks like making things seem urgent or playing on feelings to get people to fall for the scam.
Phishing attacks can lead to serious problems, such as identity theft and financial fraud. Knowing about this threat can help protect you and your group from its negative effects.
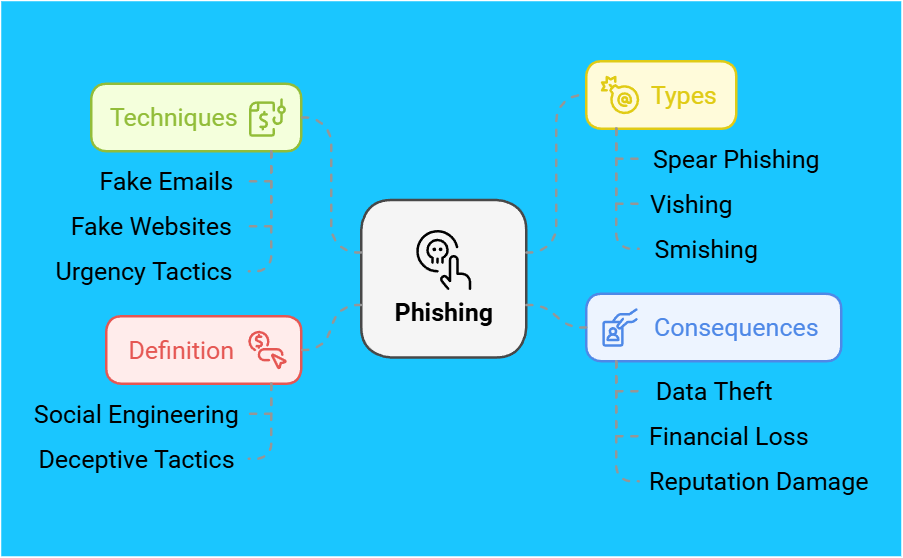
Common Phishing Attacks and Their Consequences
Phishing attacks are a big problem in today’s cybersecurity world. They are a common way hackers try to trick people. These scams can hit both individuals and businesses hard. They can lead to data theft, loss of money, harm to reputations, and even identity theft.
Spear phishing is a sneaky type of phishing. Hackers send fake emails that look like they’re from someone you trust. These emails might ask for personal info or get you to download something harmful. If you fall for it, you could lose important data or money.
Vishing is another type of phishing that uses phone calls. Scammers pretend to be from a trusted place like a bank. They try to get you to give out personal info or do something risky. This can lead to big financial losses and stolen personal data.
Smishing is when scammers use texts to trick you. They might send a message that looks urgent or interesting. If you click on a link or do what they say, you could end up in trouble. This could mean losing your identity or money.
Phishing attacks can cause a lot of harm. They can lead to losing data, money, and trust. It’s important to know how these attacks work to protect yourself. Understanding phishing is key to fighting this growing threat.
By being careful and teaching others about phishing, we can reduce the risks and protect ourselves from these harmful attacks.
Read More: Top 10 Most Common Types of Cyber Attacks
Real-Life Phishing Examples: A Cautionary Tale
In today’s digital world, we face constant threats from internet safety and social engineering tricks. Phishing is a common internet scam that worries both people and companies. By looking at real examples, we can learn how cybercriminals work and protect our online security.
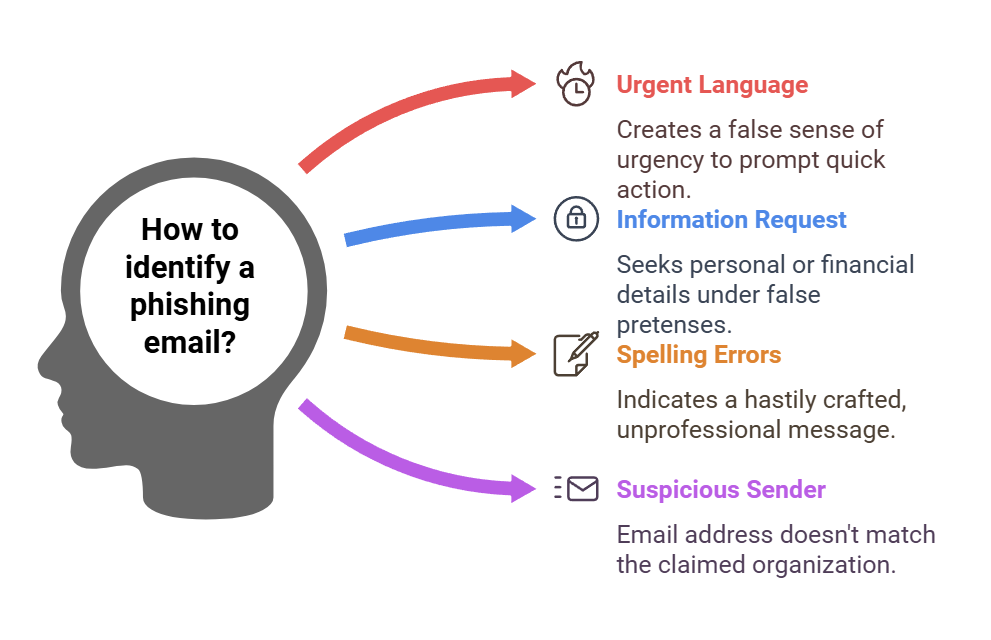
Phishing Email Scams: Recognizing the Red Flags
Phishing emails try to trick us by pretending to be from trusted sources. They might look like they’re from banks, government agencies, or famous companies. They aim to get us to share private info, like passwords or bank details. These emails can look real, with official logos and urgent messages.
Here are signs to spot phishing emails:
- Urgent or threatening language that creates a sense of urgency
- Requests for personal or financial information, even from seemingly trustworthy sources
- Spelling and grammar errors, which are common in hastily crafted phishing messages
- Suspicious sender email addresses that don’t match the purported organization
Read More: What are the 4 types of cyber threats?
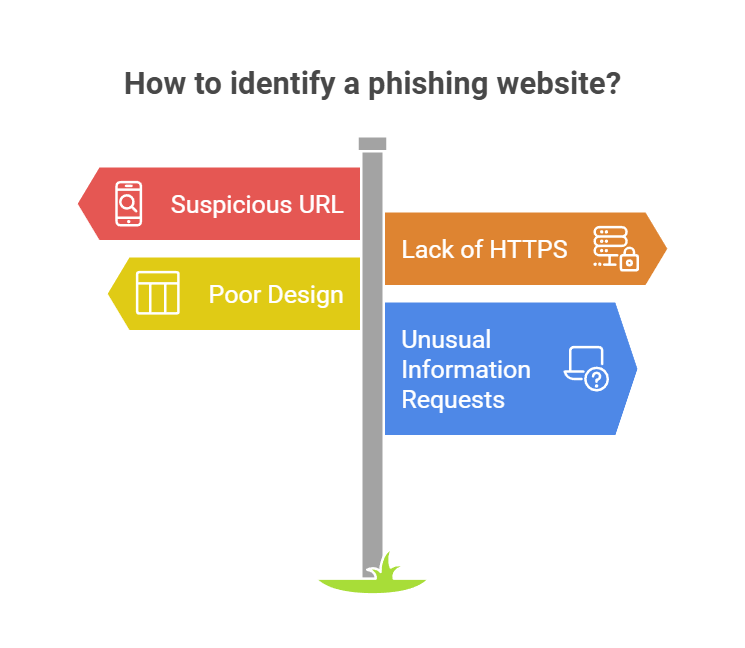
Phishing Websites: Spotting the Impostors
Cybercriminals also use fake websites for their scams. These sites pretend to be real online places, like banks or shopping sites, to steal our info. It’s important to know how to spot these fake sites to keep our online safe.
Here are signs of a phishing website:
- Suspicious or altered URL, often with minor variations from the legitimate website
- Lack of a secure HTTPS connection, which is standard for reputable websites
- Poor design, low-quality images, or outdated branding elements
- Requests for sensitive information that the legitimate website would not ask for
Learning from real phishing examples helps us protect ourselves. By staying alert and following online security tips, we can avoid the harm of social engineering attacks and data breaches.
What Is Phishing?
In today’s digital world, phishing is a big threat. Criminals use tricks to get your info. They aim to steal your identity or money. This is done through social engineering attacks.
Phishing attacks come in many forms, like fake emails or texts. They look like they’re from trusted places like banks or government agencies. The goal is to get you to share your login details or sensitive info.
Cybercriminals are always finding new ways to trick us. They use email phishing and phishing websites that look real, making it hard to stay safe online.
It’s important to know how phishing works and its risks. By being aware and taking steps to protect ourselves, we can fight back against these threats. This helps keep our online identities safe from phishing scams and identity theft.
Read More: What is Cybersecurity? Types, Threats, and Cyber Safety Tips
Defending Against Phishing: Proactive Measures for Individuals and Organizations
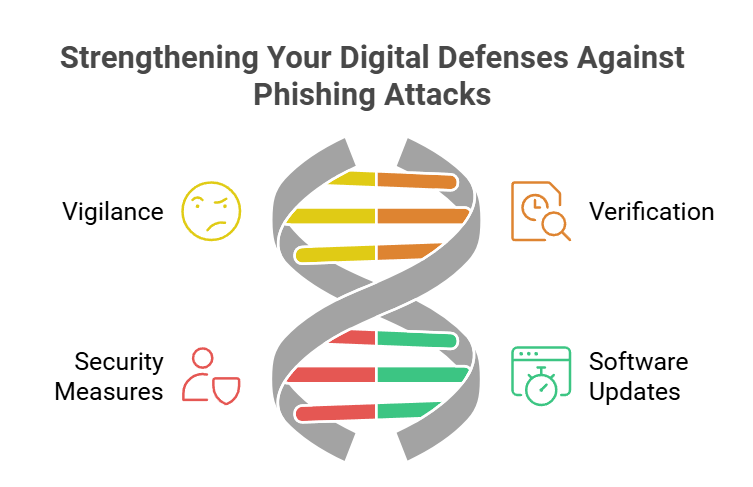
Phishing attacks are a big threat in our digital world, targeting both people and companies. Protecting your online stuff and personal info needs a strong plan. This plan should include being alert, learning, and using the latest anti-phishing tools.
Phishing Prevention Tips: Staying Vigilant Online
You can take steps to protect yourself from phishing. First, be careful with unsolicited emails, texts, or social media messages that ask for your private info or make you click on shady links. Always check who sent the message, and be cautious of urgent or scary messages.
- Look closely at email addresses and domain names for any mistakes or misspellings that might show a phishing scam.
- Please don’t click on links or open attachments from people or places you don’t know, as they could have malware or take you to fake sites.
- Use two-factor authentication on your accounts to make it harder for hackers to get in.
- Keep your software and systems updated to get the newest security fixes and protection.
Anti-Phishing Solutions: Safeguarding Your Digital Assets
Companies need to act fast to fight phishing attacks. Using strong anti-phishing steps can protect important data, keep your brand’s good name, and avoid the bad outcomes of a phishing attack.
| Anti-Phishing Solution | Description | Key Benefits |
|---|---|---|
| Email Filtering and Monitoring | Advanced email security tools that check incoming messages for phishing signs and block bad content. | Keeps phishing emails out of employee inboxes, lowering the chance of data theft and cyber-attacks. |
| Website Reputation Monitoring | Tools that always check the web for fake sites that look like the company’s brand or domain. | Fastly finds and takes down phishing sites, protecting the company’s online image and customer trust. |
| Phishing Awareness Training | Thorough training that teaches employees about the latest phishing tricks and how to spot and report suspicious stuff. | Trains employees to be the first ones to stop phishing attacks, creating a strong cybersecurity culture. |
By using proactive steps for people and strong anti-phishing tools for companies, we can all get better at fighting phishing attacks. This helps protect our digital stuff in a world that’s always changing.
Conclusion
In this article, we explored the complex world of phishing, a growing cyber threat harming people and businesses. We covered what phishing is, the methods attackers use, and real examples of scams.
Phishing uses malicious links and hacking techniques to trick people. It’s important to know how to spot and prevent these attacks. We talked about why phishing awareness and cybersecurity threat prevention are key.
Staying alert and knowing the signs of phishing can help protect you. Understanding the threat and taking steps to secure your digital life can help you fight back against phishing. This is the first step towards a safer online world.
FAQ
What is phishing?
Phishing is a sneaky way hackers use fake emails or websites to get your info. They trick people into sharing sensitive details or doing things that put their security at risk. Hackers use tricks to make you trust them and steal important data like passwords or financial info.
What are the different types of phishing attacks?
There are a few ways phishers can trick you: – Spear phishing targets you by pretending to be someone you know, like a coworker. – Vishing is when they call you and try to get you to give out info. – Smishing is through texts, trying to get you to click on links or give out info. – Pharming tricks you into visiting a fake site that looks real, often through a trick with your internet settings.
Can you provide some examples of phishing attacks?
Sure, here are some real phishing examples: – A fake email from a bank asking you to check your account info. – A website that looks like a login page but isn’t, trying to get your password. – A text saying you won a prize and asking for your details.
How can I prevent myself from falling victim to a phishing attack?
Here’s how to stay safe: – Be wary of emails, messages, or calls asking for your private info without a good reason. – Always check if the request is real by contacting the company the right way. – Watch out for emails with mistakes, generic greetings, or weird URLs. – Use anti-phishing tools and keep your devices updated. – Learn about phishing and teach others in your company how to spot it.
What can organizations do to protect against phishing attacks?
Companies can fight phishing by: – using strong email security and spam filters. – teaching employees about online safety and phishing. – Extra security checks are used to protect against stolen passwords. – Watch for and fix any suspicious activity or data leaks. – testing their defenses with fake phishing attacks.
How does phishing differ from other cyber threats?
Phishing is unique because it uses tricks to get what it wants, not just tech weaknesses. It usually targets people, not just the company’s tech. The main goal is to get sensitive info, not to mess with systems or operations.






