What are the four types of IT Security?

What are the four types of IT Security? 2024
Today’s world is all about technology. It’s in everything we do. So, what are the four types of IT Security? IT security is more complex. It uses many strategies and tools to keep organizations safe from cyber threats. There’s network, endpoint, application, and cloud security. Each is vital for keeping data secure and ensuring digital systems work well.
Network security is key. It protects the inner workings of networks from unauthorized access and ensures that computers, users, and programs work securely. The main aim is to prevent unauthorized people or devices from entering.
Endpoint security makes sure only trusted devices can join a network. As more devices join, the threats increase. Internet security, or cybersecurity, focuses on data traveling safely online. It uses techniques like encryption with SSL and TLS to keep data safe.
With cloud computing becoming more popular, cloud security is crucial. The approach needs to have many layers to protect every part of the cloud. As tech grows, companies must have a strong IT security plan. This will keep their digital assets safe from various cyber threats.

Key Takeaways
- IT security includes network security, endpoint security, application security, and cloud security.
- Network security protects networks from unauthorized access and misuse.
- Endpoint security makes sure only trusted devices can access systems to avoid breaches.
- Cybersecurity focuses on the safety of data as it moves online, using encryption.
- Cloud security uses multiple layers to defend data and systems in the cloud.
Introduction to IT Security
Since the start of the 21st century, the digital world has changed a lot. Information Technology (IT) now covers more than searching the web or using old computers. It includes many things like programming, security, and data analysis. Because of this growth, IT security has become very important. It helps protect a business’s information and daily work. The field of IT security has evolved significantly over the years, from basic antivirus software to complex network security systems. As technology continues to advance, so do the threats, making it crucial for businesses to stay updated on the latest security measures.
Defining IT Security
IT security is wider than just fighting cybercrime. It aims to keep all types of data safe, whether digital or physical. Cybersecurity focuses on crimes that use the internet. Even though they are a bit different, IT security and cybersecurity both protect important information. However, the implementation of IT security measures can also raise ethical and legal questions. For instance, the use of surveillance tools to monitor employees’ online activities can be seen as an invasion of privacy. Organizations need to strike a balance between protecting their data and respecting the rights of their employees.
Importance of IT Security in the Digital Age
Digital tools now play a big role in business and daily life. They can do complex tasks and store a lot of data. Protecting this data and the systems it’s on is very important for every organization. It ensures businesses can keep running, their data stays private, and they are safe from online threats. Looking ahead, the increasing use of IoT devices and the growing sophistication of cyber threats pose new challenges for IT security. Organizations need to stay vigilant and adapt their security measures to these evolving trends.

Network Security
Network security is about how devices interact. It focuses on keeping the networking system safe, which prevents unauthorized access, misuse, or change in the network’s hardware and software.
Its main aim is to prevent unknown people or devices from getting in.
Access Control Systems
Access control systems, firewalls, and VPNs are crucial for network safety. Access systems check who users are and then allow specific users to use certain parts of the network, ensuring only the right people do so.
They help keep a company’s IT and important data safe from intruders.
Firewalls
Firewalls act as a guard between safe and unsafe networks. They check and decide which traffic to allow or not. This way, they protect against malicious software and unauthorized users.
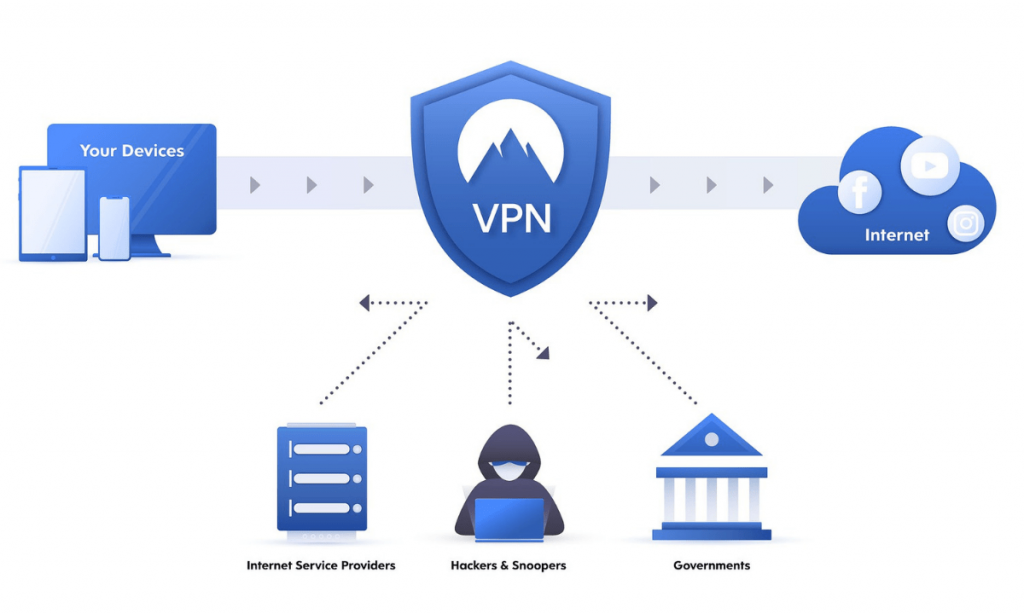
Virtual Private Networks (VPNs)
VPNs create safe connections for data between devices. They keep data safe while it moves through public pathways, helping to secure remote working and outside offices.
A security framework, like NIST’s guidelines, ensures best practices. It keeps networks safe and stops new cyber dangers.
Endpoint Security
Endpoint security is all about keeping network devices safe. It makes sure only the right devices can access data. When a new device connects, the risk goes up, so security software might block risky apps, control data, and spot any threats. This can include using encryption to keep data safe while it moves. Plus, it covers the user’s device and the company’s main system. This way, they keep the whole network safer with updates and by watching how users use devices.
Antivirus and Anti-malware Software
Antivirus and anti-malware are big parts of keeping devices secure. They catch and stop harmful software. These tools need to stay up to date to fight the latest threats. They protect against many types of attacks, like ones that change or happen without warning.
Encryption and Data Protection
Endpoint security also defends against losing or leaking data. It uses encryption and checks user behavior to keep data safe. Strong encryption means only the right people can see data. Endpoint security lets big organizations keep an eye on everything. They can control, check, and react to threats from many endpoints at once, making it easier to spot and handle issues quickly.
IT Security
IT security is about protecting data, systems, and infrastructure. Cybersecurity is more specific, focusing on internet threats. The CIA acronym stands for confidentiality, integrity, and availability. It’s a core part of IT security.
Principles of Confidentiality, Integrity, and Availability
Confidentiality ensures that only the right people see sensitive data. Integrity keeps information correct and complete. Availability means authorized users can access data and resources easily and quickly. These are key to keeping an organization safe.
Role of IT Security Professionals
IT security professionals play a pivotal role in maintaining the safety of digital assets. Their expertise and strategies, such as access controls, encryption, firewalls, and incident response plans, are instrumental in this process. They are responsible for identifying and rectifying vulnerabilities, managing security incidents, and ensuring adherence to security protocols. Their knowledge is invaluable in the face of the increasing complexity of cyber threats.
Application Security
Application security is all about keeping the software we use safe. It makes sure programs are built with security from the start. A Secure Software Development Life Cycle (SDLC) is key here. It puts security checks in place at every step of building an app.
Web Application Firewalls (WAFs) play a big role, too. They watch the traffic coming into a website. This helps them catch and stop experts in hacking (hackers) from using tricks like SQL injection or cross-site scripting (XSS). Keeping security tight at the app level protects what’s important from bad actors.
Secure Software Development Life Cycle (SDLC)
The Secure Software Development Lifecycle (SDLC) is a full approach to ensuring software safety. It means thinking about security from the very first step, not just at the end. This early focus can catch problems before they become a way in for hackers.
This way, ARK Solvers makes security matter all the time. From the idea to the launch of an app, each step is built with security checks, making each app safer for everyone to use.
Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) are important for keeping apps safe, too. They look at the traffic coming to a website or app. WAFs spot and stop attacks that try to mess with the program, like SQL injections and XSS.
Having a WAF means apps and websites are more secure. It helps protect what’s inside, like data, from hackers looking for weak spots.
Cloud Security
The rise of cloud computing means we’ve had to rethink how we keep things safe online. Now, the lines of defense stretch far beyond our physical walls. Just like how we protect our data inside a building, we guard it closely as it moves between places. Still, the wider reach of the cloud means we have to add extra layers of security.
Cloud Access Security Brokers (CASBs)
Think of Cloud Access Security Brokers (CASBs) as gatekeepers. They stand between us, the users, and the clouds we use. Their job is to ensure that only the right people get in while monitoring for any leaks of important data.
This extra layer of security makes it easier for companies to monitor their online activities. It means they can be sure that only the right people touch their data and that it doesn’t slip out where it shouldn’t.
Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) tools do a unique job. They check if a company’s online layouts are safe or if they’re open doors for trouble. If they spot any mistakes, they help companies fix them before bad things can happen.
With these tools, security teams can keep their online spaces locked up tight. This way, companies can enjoy all the benefits of the cloud without worrying about their secrets getting out. It’s all about staying on top of things every step of the way.
Data Security
Data security is a key part of IT security. It aims to keep an organization’s important information safe, including data that’s saved, used, or sent. It’s crucial in today’s world, where cybercriminals try to steal valuable information. With a strong data security plan, companies reduce the chance of a cyberattack, lowering the risk of losing money and harming their reputation.
Data Encryption
Data encryption changes data into a secret code. It makes sure only the right people can read it. This keeps info like customer details or financial data safe. Technologies like AES and RSA are important for this. They help keep data safe when it’s not being used and when it’s being sent.
Data Loss Prevention (DLP)
DLP helps prevent sensitive data from being shared accidentally or on purpose. It prevents things like financial reports and customer information from going where they shouldn’t. This can happen through emails, websites, or cloud storage.
By using DLP, organizations make their essential data safer. This reduces the risk of important information being misused.
Backup and Disaster Recovery
It is very important to back up data and be ready for a disaster. This ensures a company can access and recover its data if something bad happens. With increasing threats like ransomware, good backup and recovery plans are a must. They can save businesses from major troubles.
Companies like Veeam, Druva, and Acronis help with this. They provide good backup and recovery options, which keep a company going even after a bad event.
Conclusion
In the world of information technology, IT security is more crucial than ever. Cyber attacks are getting more complex. This makes it vital for all organizations to have strong IT security measures.
The team at ARK Solvers works hard to keep their client’s networks and data safe. They focus on key areas like network, endpoint, application, and cloud security. This approach ensures your digital info remains confidential, integral, and available. Our IT experts are dedicated to finding and fixing security weaknesses. They also monitor and respond to security threats and meet industry regulations.
Technology is always changing, so staying ahead in IT security is a must for both businesses and individuals. This means always learning, assessing, and having plans in place for when things go wrong. Strong cyber protection is built on awareness and quick response. ARK Solvers helps its clients keep up with changing IT security needs. They help businesses protect their digital investments for the long term.
FAQ
What are the four primary types of IT security?
IT security has four main types: network, endpoint, application, and cloud security. They keep our digital world safe.
What is the goal of network security?
Network security aims to keep our digital highways safe. It protects the links between devices from bad actors, ensuring a safe space for all online activities.
What is the focus of endpoint security?
Endpoint security makes sure only verified devices connect to networks. It’s like a bouncer for all incoming online guests. This way, we keep the digital party secure.
How does application security protect software applications?
Application security shields the software we use from online dangers. It ensures programs are born with a shield, protecting your info. This is done through smart development and using special guards.
What is the role of cloud security in protecting data and systems?
The rise of cloud computing made a new guard necessary. Cloud security keeps data safe in shared spaces, preventing cyber sneak-ins. It works by checking the system’s armor and improving it.
How does data security protect an organization’s sensitive information?
Data security is the shield for an organization’s secrets. It turns information into secret code, watches over its moves, and has a plan B ready. All to keep secrets safe and sound.
What are the core principles of IT security?
The heart of IT security follows three rules: keep secrets secret, ensure information is true, and let the right people in. It’s like a digital handshake, ensuring trust in our tech.