Different Types of Cyber Security: A Comprehensive Guide
Ever wonder how our digital world stays safe from threats? Cyber attacks are getting more complex, making it key to know about cyber security types. This guide explores how digital protection works, showing us how to keep our online lives safe.
Cybersecurity is more than just a buzzword; it’s essential in our connected world. It helps protect sensitive data and whole networks. But what does cyber security mean? It’s about defending computers, servers, mobile devices, and networks from harmful attacks.
Strong cyber security is vital in today’s digital age. This guide will explain the different types of cyber security and explain how each one is important for keeping us safe online.
Key Takeaways
- Cyber security protects digital assets from various threats
- Different types of cyber security address specific vulnerabilities
- Network and application security form the backbone of digital protection
- Cloud security is essential in today’s remote work environment
- Data encryption and access management are crucial for information safety
- IoT security is becoming increasingly important as connected devices proliferate

Introduction to Cyber Security
Cyber security is very important in our digital world. It keeps our online presence safe from threats. Understanding cyber security is essential to staying safe online.
What is Cyber Security?
Cyber security is about protecting computer systems, networks, and data from digital attacks. It prevents unauthorized access and data breaches and ensures our digital assets are safe and available.
Read More: What is Cybersecurity? Types, Threats, and Cyber Safety Tips
The Importance of Cyber Security in Today’s Digital Landscape
Cyber security is crucial in our connected world. It keeps our personal and financial information safe. Think of it as a digital lock for your online life.
Without it, we’d be open to many digital threats.
Evolution of Cyber Security Threats
Cyber threats have changed a lot over time. Early threats were simple viruses. Now, we face complex attacks like:
- Ransomware
- Phishing scams
- Advanced persistent threats
These threats need us to stay alert. As technology gets better, so do the ways cybercriminals attack. It’s important to keep up with these threats to protect ourselves.
Network Security: Protecting Your Digital Infrastructure
Network security is key to keeping data safe from hackers and unauthorized access. It helps protect computer networks and data from threats. Knowing about different cyber security methods is vital for companies today.
Firewalls are the first defense against cyber threats. They check and control what data goes in and out of a network. Intrusion Detection Systems (IDS) also help by spotting and alerting about suspicious activities.
Virtual Private Networks (VPNs) are crucial for keeping data safe. They encrypt data sent over public networks, so even if hackers try to intercept it, they won’t be able to read it.
Network segmentation is another important security step. It breaks a network into smaller parts, making it harder for hackers to spread if they get in and improving the network’s performance.
- Implement robust firewalls
- Use Intrusion Detection Systems
- Employ Virtual Private Networks
- Apply network segmentation
- Conduct regular network monitoring
Knowing about the seven layers of cyber security is key to full protection. These layers cover everything from physical security to data encryption. By securing each layer, companies can effectively fight off cyber threats.
Read More: What is Network Security? Definition, Importance, and Types
Application Security: Safeguarding Software and Systems
Application security is key to defending against cyber threats. It keeps software and systems safe from various attacks. Let’s look at the main areas of application security and how they fight off cyber attacks.
Web Application Security
Web apps are at risk. Hackers aim to steal data or disrupt them. A detailed check for weak spots is crucial. Common ways to protect include:
- Input validation
- Authentication controls
- Regular security updates
Mobile Application Security
Mobile apps require special security steps. They hold sensitive data and connect to networks. Important steps for mobile app security are:
- Secure data storage
- Encryption for data in transit
- Regular code reviews
API Security
APIs link different software systems. They need strong protection to stop unauthorized access. Good API security includes:
- Authentication and authorization
- Rate limiting
- Encryption of sensitive data
Keeping application security up to date is vital. It needs constant attention and updates to beat new threats. Regular checks and finding vulnerabilities are key to strong defense against cyber attacks.
Read More: What is Application Security? – Types, Tools & Best Practices
Cloud Security: Securing Data in the Virtual Environment
Cloud security is key in today’s digital world. As companies move to the cloud, keeping data safe gets harder. Clouds have many benefits but also bring new challenges for protecting data.
To tackle these issues, companies use various cloud security steps:
- Data encryption
- Access control systems
- Regular security audits
- Network monitoring
These measures help build a strong defense against threats. Cloud providers are key in this effort. They offer built-in security and work with users to keep the cloud safe.
The shared responsibility model is important in cloud security. It splits security tasks between the cloud provider and the user. Providers handle the infrastructure while users protect their data and apps.
Disaster recovery is also vital in cloud security. Cloud backup and recovery solutions help keep businesses running if data is lost or systems fail. With strong cloud security steps, companies can use cloud computing safely and reduce risks.
Read More: What is Cloud Security? – Defining The 6 Pillars & Benefits
Data Security: Protecting Sensitive Information
Data security is key to keeping information safe. It protects digital data from unauthorized access, damage, and theft. With cyber threats becoming more complex, strong data protection is a must.
Data Encryption
Encryption changes readable data into a secret code, making it unreadable to others without the right key. Strong encryption keeps sensitive data safe when stored or sent, lowering the chance of data theft.
Data Loss Prevention (DLP)
DLP strategies stop data leaks and keep sensitive info from being shared without permission. These tools watch, find, and block data breaches. They’re crucial for keeping data safe in places that handle private info.
Database Security
Keeping databases safe is key to protecting lots of sensitive data. This includes:
- Access controls
- Regular security checks
- Data masking
- Backup and recovery plans
By using these steps, companies can greatly lower the risk of cyber attacks. Remember, keeping data secure is an ongoing task that needs constant attention and updates to stay ahead of new threats.
Read More: What Is Data Security? – Definition, Explanation and Guide
Identity and Access Management: Controlling User Privileges
Identity and access management (IAM) is key to modern cybersecurity. It helps control who can access sensitive data, and companies can lower the risk of cyber attacks by using strong IAM practices.
Authentication is a big part of IAM. It includes:
- Passwords
- Biometrics
- Multi-factor authentication
Authorization makes sure users only see what they need for their job. This keeps the system secure. Role-based access control (RBAC) helps manage who can do what in an organization.
IAM also helps with following the law and managing access. It keeps track of who did what and enforces rules. This is vital in fields with strict data laws.
Strong IAM solutions boost a company’s cybersecurity. They protect against unauthorized access and make managing users easier. This improves both security and efficiency.
Read More: What is Identity and Access Management? Guide to IAM
Endpoint Security: Defending Devices and Workstations
Endpoint security is key in our digital world. It shields devices from cyber threats when they connect to your network, including computers, smartphones, and tablets. Let’s look at the main parts of endpoint security.
Antivirus and Anti-malware Solutions
Malware protection is the first defense. Antivirus software looks for and removes harmful programs. It fights against viruses, trojans, and other bad code. Now, modern solutions use AI to find new threats fast.
Endpoint Detection and Response (EDR)
EDR goes beyond basic security. It watches endpoints for odd activities. If it finds a threat, EDR acts quickly. It can lock down infected devices to stop attacks from spreading. This quick action is crucial for businesses.
Mobile Device Management (MDM)
Mobile security is a must in our smartphone era. MDM tools help manage mobile devices. They can:
- Enforce password policies
- Encrypt data on devices
- Remotely wipe lost or stolen phones
- Control app installations
Good endpoint security uses these tools. It fights against malware, spots threats, and manages mobile devices. This full approach keeps your network safe in our fast-changing digital world.
Read More: What Is Endpoint Security? How It Works & Its Importance
Different Types of Cyber Security
Cyber security covers many specialized areas. Organizations must know the different types to protect against digital threats. Let’s look at the five main types that are key to digital safety.
The five types of cyber security are:
- Network Security
- Application Security
- Operational Security
- Disaster Recovery
- End-User Education
Read More: What are the five types of cyber security: Beyond the Basics
Network security protects computer networks and data. Application security keeps software and systems safe from threats. Operational security focuses on how to handle and protect data safely. Disaster recovery plans help fix things after cyber attacks. End-user education teaches employees how to spot and avoid cyber threats.
When asked, “What are the 3 major types of cyber security?” Experts say network, application, and operational security are the main parts of a strong cyber security plan. They cover the most important aspects of keeping digital information safe.
Using these five main types of cyber security, companies can build a strong defense and fight off many cyber threats. From malware and phishing to data breaches and insider threats, they’re covered.
Cryptography: Securing Communication and Data
Cryptography is key to many cybersecurity methods. It’s the science of keeping data and messages safe from unwanted eyes. In our digital age, it’s crucial to protect sensitive info from cyber threats.
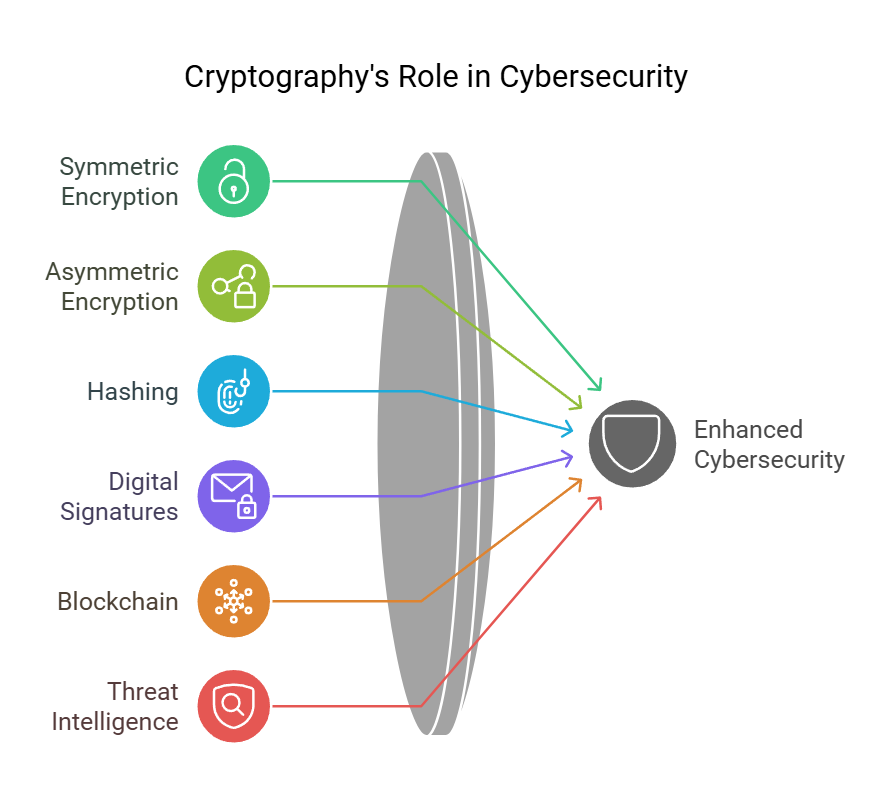
Cryptographic methods include:
- Symmetric encryption: Uses a single key for both encoding and decoding
- Asymmetric encryption: Employs public and private key pairs
- Hashing: Creates unique digital fingerprints of data
- Digital signatures: Verifies the authenticity of digital messages
These methods are vital for many cyber security tasks. Secure messages and data rely on cryptography to stay private. Encryption also protects stored data. Even blockchain, a new digital leader, uses cryptography to build trust and security.
Threat intelligence systems often use cryptography to keep their information safe. By using strong encryption, they can share data on cyber threats safely, avoiding the risk of exposing their findings to bad actors.
As cyber threats grow, so do cryptographic methods. Keeping up with the latest in cryptography is key to strong cyber security. It’s a race between security pros and cybercriminals, with cryptography as a powerful defense tool.
Read More: What is Cryptography? Definition, Importance, Types
Internet of Things (IoT) Security: Protecting Connected Devices
IoT security is key as more smart devices join our everyday lives. It covers many areas to keep devices, networks, and data safe from cyber threats.
IoT Device Security
IoT device security begins at the design stage. Makers need to include security features like strong passwords, encrypted updates, and secure hardware. Users should update their devices, change default passwords, and turn off unused features to lower risks.
IoT Network Security
Keeping IoT networks safe means segmenting devices from important systems. This limits damage if a device gets hacked. Using firewalls, intrusion detection, and VPNs adds more protection to IoT setups.
IoT Data Security
Protecting IoT data is crucial for privacy and keeping critical systems safe. Data should be encrypted when moving and when stored. Strong access controls and regular security checks prevent unauthorized data access. Companies must follow data protection laws based on their industry and location.
By focusing on these areas, both businesses and individuals can improve their IoT security. As IoT grows, staying updated on new threats and best practices is key to strong security.
Read More: What is Internet of Things Security? and Why It’s Important
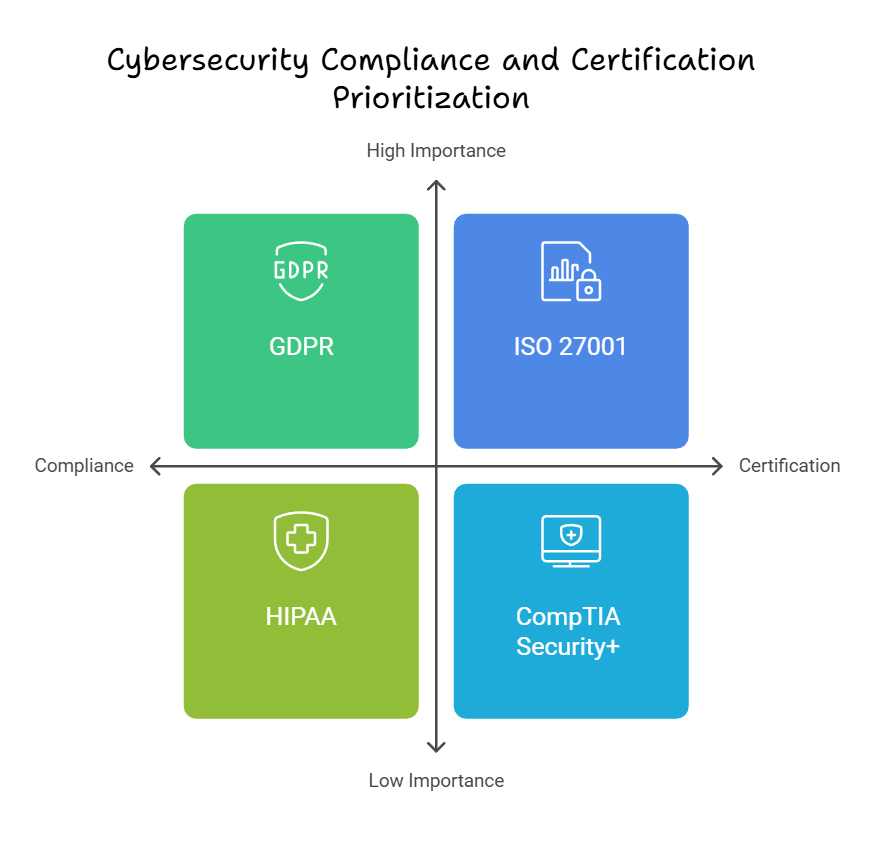
Compliance and Regulations: Meeting Industry Standards
Cybersecurity compliance and regulations are key to keeping data safe and building trust online. Companies must follow many standards to protect their data and their reputations.
- GDPR (General Data Protection Regulation)
- HIPAA (Health Insurance Portability and Accountability Act)
- PCI DSS (Payment Card Industry Data Security Standard)
These rules set the bar for protecting data, keeping it private, and keeping it secure. Following these rules is vital for managing risks and maintaining a strong security stance.
Certifications in cyber security show an organization’s dedication to top-notch practices. Some top certifications are:
- ISO 27001 for information security management
- CISSP (Certified Information Systems Security Professional)
- CompTIA Security+
Getting these certifications boosts an organization’s trustworthiness and gives it an edge in the market. They also help in making a solid risk management plan. This ensures security practices meet industry standards.
Following compliance and regulations is the base of a strong cyber security plan. By sticking to these rules, companies can better protect their assets, customers, and reputation in today’s complex digital world.
Incident Response and Disaster Recovery
Cyber attacks can happen at any time, which is why having incident response plans is key for businesses. These plans help teams react quickly when threats appear and cover important steps like preparing, detecting, containing, and recovering.
Preparation is vital. Companies need to train their staff and set up systems to spot issues fast. When an attack occurs, detecting it is the next step. This means figuring out what’s happening and how severe it is. Then, containing the threat is crucial to stop it from spreading.
Recovery is the last step. It’s about getting systems back online. Disaster recovery and business continuity plans are key here. They help a company keep running after a big cyber event.
Cyber risk management combines all these parts. It’s about always looking for and dealing with threats. By being proactive, businesses can lower their risk of cyber attacks.
- Create and test incident response plans regularly
- Develop robust disaster recovery strategies
- Implement continuous cyber risk management practices
The aim isn’t just to react to incidents. It’s to build resilience against future threats. With strong plans, businesses can tackle cyber challenges and come out stronger.
Read Relevant Blog:
- Exploring the Various Types of Cyber Security Threats
- Top 10 Most Common Types of Cyber Attacks
- What are the 4 types of cyber threats?
- What are the Three Types of Network Service Vulnerabilities?
- What are the Types of Network Security?
- What are the 4 types of IT Security?
Conclusion
Cybersecurity has many forms, each crucial for protecting our digital world. You might ask, “How many types of cyber security exist?” The answer changes as new threats emerge.
Building a strong cyber defense means combining different security types—it’s like having many walls around your fortress. Ethical hacking helps find and fix weak spots, and security experts use this method to strengthen defenses before real threats strike.
Penetration testing goes even deeper. It’s a simulated attack to see where defenses might break. As threats grow, these practices become more important. They help keep our data safe in a changing digital world.
Cyber security is not a one-time task. It’s a continuous process of learning and adapting. By staying vigilant and using various security types, we can better protect our digital lives.
FAQ
What is cyber security?
Cyber security is about keeping computer systems, networks, and data safe from hackers and other threats. It uses many methods to protect digital assets. This includes keeping data private, making sure it’s not changed, and keeping it available when needed.
Why is cyber security important in today’s digital landscape?
Today, we rely heavily on technology and the Internet. Cyber security is key to protecting our personal and business data. It helps avoid financial losses, damage to reputation, and legal issues from cyber attacks or data breaches.
What are the different types of cyber security?
Cyber security has many types, including network security, application security, cloud security, and more. It also covers data security, identity management, and protecting mobile and IoT devices.
What is network security, and why is it important?
Network security protects computer networks and data from unauthorized access and attacks. It uses tools like firewalls and VPNs to keep the network safe and help prevent cyber threats.
What is application security, and why is it crucial?
Application security keeps software and systems safe from cyber threats. It involves secure coding, testing, and controls for apps and APIs. This is very important to protect against attacks.
What is cloud security, and why is it significant?
Cloud security protects data and systems in cloud computing. It uses encryption and access controls to keep cloud resources safe and private. This is important for data security.
What is data security, and why is it essential?
Data security protects sensitive information from unauthorized access or theft. It uses encryption and other methods to keep data safe. This is crucial for keeping digital data private and secure.
What is identity and access management (IAM), and why is it crucial?
IAM controls who can access data and systems in an organization. It ensures that only authorized people can see sensitive information, reducing the risk of security breaches and helping to comply with the law.
What is endpoint security, and why is it important?
Endpoint security protects devices like laptops and phones that connect to a network. It uses antivirus software and other tools to prevent malware and data breaches. This is important for keeping devices safe.
What is cryptography, and how does it contribute to cyber security?
Cryptography uses math to secure data and communication. It’s key for protecting sensitive information and ensuring secure data transfer. It also helps in verifying identities securely.






