Essentials of Risk Management in Cyber Security Strategies 2025
Are you confident that your organization is fully prepared to handle cyber threats? In today’s digital age, the risk of cyber attacks is ever-present, making robust risk management in cyber security a necessity. Implementing effective risk management strategies is crucial for safeguarding your organization’s valuable information assets and maintaining business continuity.
This section of our article will delve into the essentials of risk management in cyber security strategies. We will explore the significance of cyber security risk analysis and discuss best practices for effectively managing risks in information security. Join us as we unravel the intricacies of cyber security risk management and equip you with the knowledge and tools to stay one step ahead of cyber threats.
Let’s start and discover how to enhance your organization’s cyber security defenses through proactive risk management!
Read More: Different Types of Cyber Security
Cyber Security Risk Assessment and Mitigation
Organizations face an ever-increasing number of cyber threats in today’s digital landscape. To effectively protect valuable digital assets, it is crucial to understand the importance of cyber security risk assessment and have robust risk mitigation strategies in place. A proactive approach to managing cyber security risks can help organizations identify vulnerabilities, implement necessary controls, and minimize potential impacts.
To initiate effective cyber risk assessment, organizations must follow a systematic process that involves identifying assets, evaluating threats, assessing vulnerabilities, and determining potential impacts. This comprehensive assessment provides valuable insights into the current state of cyber security and enables organizations to make informed decisions for risk mitigation.
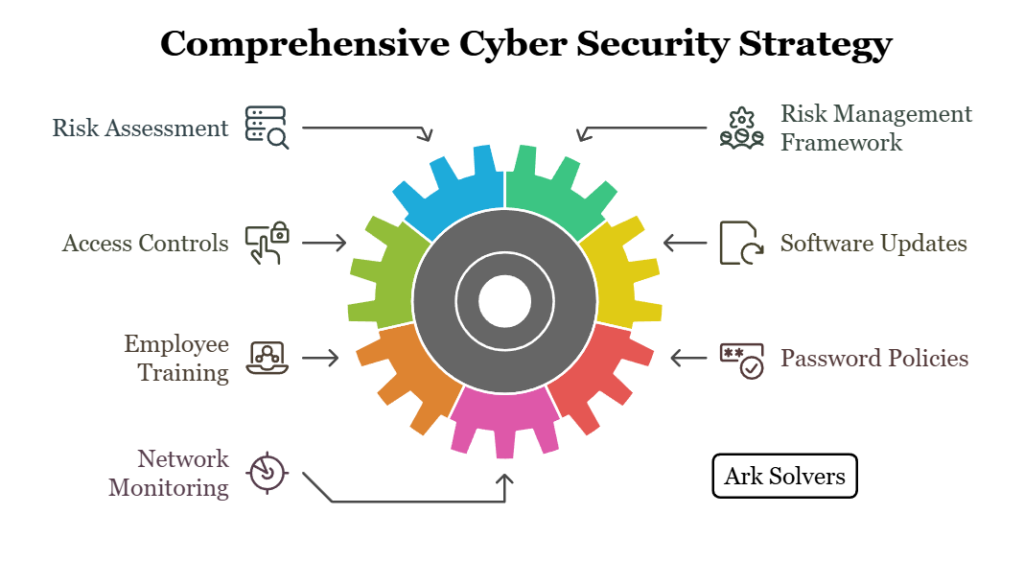
Once risks are identified and analyzed, the next step is implementing suitable risk management frameworks specifically designed for cyber security. These frameworks provide a structured approach to managing risks by establishing policies, procedures, and controls. The risk management framework for cyber security ensures that organizations have a consistent and standardized way of addressing risks, enhancing their overall security posture.
Organizations can employ several cyber security risk management strategies to mitigate identified risks effectively. These strategies may include:
- Implementing robust access controls to protect sensitive data and prevent unauthorized access
- Regularly updating and patching software to address known vulnerabilities
- Conducting thorough employee training and awareness programs to educate staff about cyber threats and best practices
- Enforcing strict password policies and implementing multi-factor authentication
- Monitoring and analyzing network traffic to identify and respond to potential security incidents
Organizations can significantly reduce the likelihood and impact of cyber attacks by adopting and integrating these strategies into their cyber security risk management framework.
Organizations must prioritize cyber risk assessment and mitigation to protect their digital assets and maintain the trust of their stakeholders. By implementing robust risk management strategies and frameworks, organizations can establish a strong security foundation and effectively navigate the complex landscape of cyber threats.
| Risk Management Framework | Benefits |
| Identifies and assesses potential risks | Enables proactive decision-making for risk mitigation |
| Establishes consistent procedures and controls | Enhances overall security posture |
| Provides a framework for ongoing risk monitoring and management | Ensures continuous protection against evolving cyber threats |
Data Protection Measures and Security Incident Response Planning
In the ever-evolving cyberspace landscape, implementing robust data protection measures is crucial to safeguarding digital assets from cyber threats. Organizations must prioritize cyber security protocols and avoid potential vulnerabilities by employing effective risk analysis techniques. Developing a comprehensive security incident response plan is essential to promptly and efficiently address and mitigate any security incidents.
At Ark Solvers, we understand the importance of data protection measures in defending against cyber attacks. Our team of experts assists organizations in establishing robust security frameworks to safeguard sensitive information and prevent unauthorized access. From implementing encryption technologies to securing networks and databases, we strive to ensure our clients’ data’s confidentiality, integrity, and availability.
Cyber security protocols are crucial in mitigating risks and preventing cyber threats. Our experts work closely with organizations to develop and implement tailor-made protocols covering all information security aspects. By establishing strong authentication mechanisms, conducting regular vulnerability assessments, and enforcing secure coding practices, we help our clients create a resilient security posture.
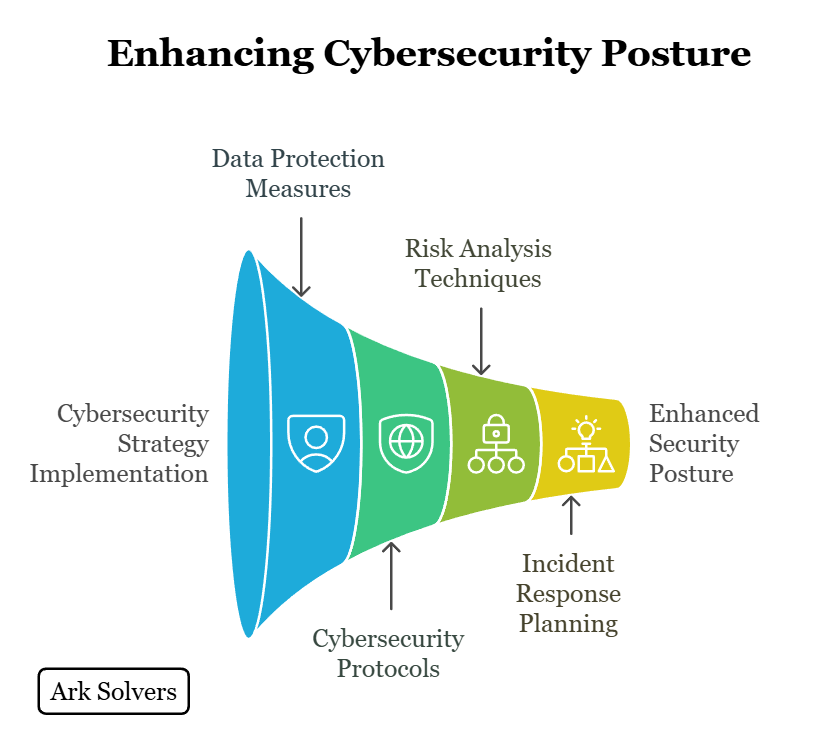
Effective Risk Analysis Techniques
Risk analysis is an integral part of cyber security strategy. Our team at Ark Solvers utilizes industry-leading techniques to identify vulnerabilities and assess the severity and impact of potential risks. By conducting comprehensive risk assessments, including threat modeling, vulnerability scanning, and penetration testing, we provide organizations with valuable insights to prioritize and address security gaps effectively.
Security Incident Response Planning is another critical aspect of any robust cyber security strategy. At Ark Solvers, we help organizations develop customized incident response plans tailored to their specific needs. From establishing incident response teams to defining incident escalation and communication protocols, we enable our clients to respond swiftly and effectively to security incidents, minimizing damage and ensuring business continuity.
By partnering with Ark Solvers and implementing data protection measures, cyber security protocols, risk analysis techniques, and security incident response planning, organizations can enhance their overall security posture and proactively defend against cyber threats.
Conclusion
In conclusion, this article has provided an overview of the essentials of risk management in cyber security strategies. By implementing effective cyber security risk assessment techniques, managing and mitigating cyber security risks, and adopting a comprehensive risk management framework, organizations can proactively protect their digital assets and minimize the impact of cyber threats.
In today’s ever-evolving cybersecurity landscape, organizations must prioritize risk management. Organizations can identify potential vulnerabilities and implement appropriate risk mitigation measures by conducting regular cyber security risk assessments. This proactive approach allows for the ongoing security and resilience of digital infrastructures.
Ark Solvers, a leading provider of cyber security solutions, offers comprehensive risk management services, including risk assessment, managing risks, and implementing a robust cyber security risk management framework. With our expertise and cutting-edge technologies, we help organizations proactively manage and mitigate cyber threats, ensuring the protection and integrity of their valuable digital assets.
FAQ
What is the importance of risk management in cyber security?
Risk management is crucial in cyber security as it helps organizations identify, assess, and prioritize potential risks to their digital assets. By implementing effective risk management strategies, organizations can proactively protect themselves from cyber threats, minimize vulnerabilities, and ensure their information systems’ ongoing security and resilience.
What are the best practices for risk management in cyber security?
Some essential best practices for risk management in cyber security include conducting regular risk assessments, implementing robust security measures, training employees on cyber security protocols, regularly updating and patching software and systems, implementing strong access controls, and developing a comprehensive incident response plan. These practices can help organizations effectively manage and mitigate cyber security risks.
How can organizations perform cyber security risk analysis?
Cyber security risk analysis involves assessing and evaluating potential information systems and digital assets risks. This process typically includes identifying assets at risk, assessing vulnerabilities and threats, quantifying the potential impact of risks, and prioritizing risk mitigation efforts. Organizations can use various techniques such as asset valuation, threat modeling, vulnerability assessment, and consequence analysis to perform cyber security risk analysis.
Why is it important to have a risk management framework for cyber security?
A risk management framework tailored for cyber security is essential as it provides a structured and systematic approach to identifying, assessing, and managing cyber security risks. It helps organizations establish consistent risk assessment methodologies, implement appropriate risk mitigation strategies, and ensure compliance with relevant regulations and industry standards.
How can organizations effectively mitigate cyber security risks?
Organizations can effectively mitigate cyber security risks by implementing technical and procedural measures. These may include implementing robust access controls, regularly updating and patching software and systems, implementing multi-factor authentication, conducting regular employee training on cyber hygiene practices, establishing incident response plans, and monitoring and analyzing security logs and alerts.






