What Does Cybersecurity Do for Personal Data Protection?
Welcome to Ark Solvers, where we delve into the fascinating world of cybersecurity and its crucial role in safeguarding personal data from online threats. In this article, we will explore cybersecurity measures’ functions, benefits, and impact, illuminating how they protect our sensitive information in the digital age.
Have you ever wondered What Does Cybersecurity Do for Personal Data Protection? How do these measures work to keep your information safe from cybercriminals, hackers, and other malicious actors? Let’s uncover the answers together and discover cybersecurity’s indispensable role in our everyday lives.
Key Takeaways:
- Understanding the functions and purpose of cybersecurity
- The importance of investing in cybersecurity measures
- The various roles and responsibilities within the cybersecurity field
- The different technologies and solutions used to protect personal data
- The positive impact and benefits of cybersecurity implementation

Understanding Cybersecurity
Before delving into the specific functions and practices of cybersecurity, it is crucial to clearly understand what cybersecurity is and why it is essential in today’s digital landscape.
Cybersecurity, also known as information security, protects computer systems, networks, and data from unauthorized access, theft, or damage. Its purpose is to safeguard sensitive information, such as personal data, financial records, and intellectual property, from cyber threats and attacks.
Read More: What is Cybersecurity? Types, Threats, and Cyber Safety Tips
The role of cybersecurity is multifaceted, encompassing both proactive and reactive measures. Proactively involves identifying potential vulnerabilities and implementing preventive measures to minimize the risk of security breaches. It consists of detecting and responding to attacks, mitigating their impact, and recovering from any damages.
Effective cybersecurity practices are crucial for organizations and individuals alike. They help ensure the confidentiality, integrity, and availability of sensitive information, maintaining digital trust and protecting against online risks.
Read More: Different Types of Cyber Security
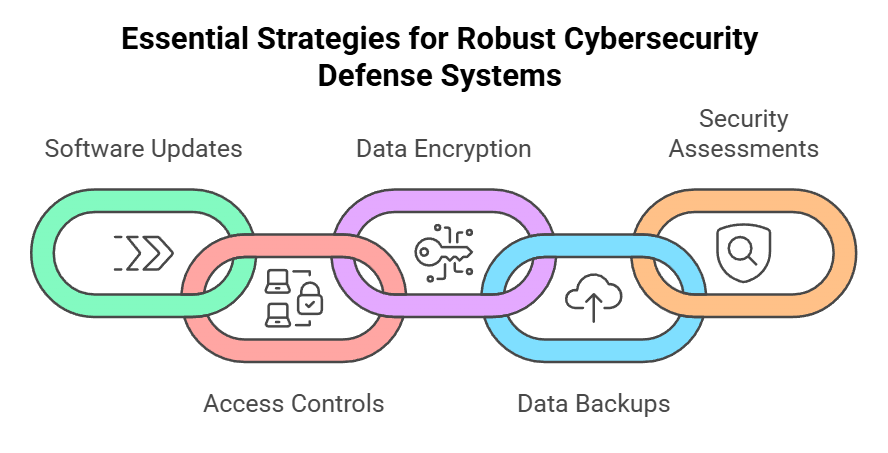
Common cybersecurity practices include:
- Regularly updating software and systems to patch vulnerabilities
- Implementing strong access controls, including unique usernames and passwords
- Encrypting data to protect its confidentiality
- Performing regular backups to ensure data availability
- Conducting regular security assessments and audits to identify potential weaknesses
- Providing cybersecurity awareness training to educate users about common threats and best practices
Why is Cybersecurity Important?
In today’s digital landscape, the importance of cybersecurity cannot be overstated. With the increasing prevalence of online threats, individuals and businesses face potential risks and vulnerabilities that can compromise sensitive data and lead to devastating consequences. Investing in cybersecurity measures is crucial for safeguarding information and maintaining online security.
Cybersecurity is particularly important for businesses, regardless of their size or industry. A data breach or cyber-attack can have severe financial and reputational repercussions, leading to loss of customer trust, legal liabilities, and disrupted operations. Implementing robust cybersecurity practices can help mitigate these risks and protect valuable assets.
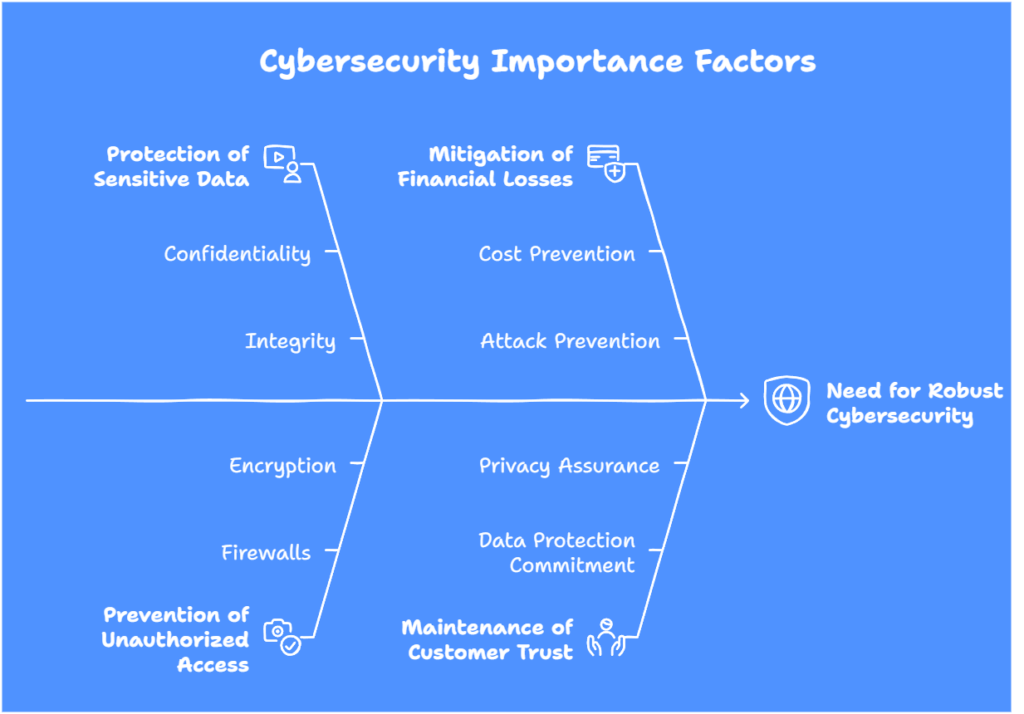
Cybersecurity is important for several key reasons:
Protection of Sensitive Data:
Cybersecurity measures ensure the confidentiality, integrity, and availability of sensitive information, such as financial records, personal data, and intellectual property. Organizations can protect these assets from unauthorized access and prevent data breaches by implementing strong security protocols.
Prevention of Unauthorized Access:
Hackers and cybercriminals constantly attempt to exploit vulnerabilities to gain unauthorized access to systems and networks. Cybersecurity measures, such as firewalls, encryption, and multi-factor authentication, help prevent these unauthorized access attempts, safeguard critical data, and protect against unauthorized use or manipulation.
Mitigation of Financial Losses:
Recovering from a cyber-attack can be costly. Organizations often incur significant financial losses due to data breaches, including expenses associated with incident response, forensic investigations, legal actions, and system repairs. Cybersecurity measures help businesses minimize financial losses by preventing such attacks in the first place.
Maintenance of Customer Trust:
Customers expect businesses to protect their personal information and maintain their privacy. Organizations prioritizing cybersecurity demonstrate their commitment to data protection, enhancing customer trust and loyalty. It contributes to a positive brand reputation and sustainable business growth.
Read More: Why is Cyber Security Important for Modern Business Safety?
It is important to note that the need for cybersecurity extends beyond businesses. Individuals are also vulnerable to cyber threats like identity theft, phishing attacks, and malware infections. By practicing good cybersecurity habits, such as using strong passwords, regularly updating software, and being cautious of suspicious emails and websites, individuals can protect their data and reduce the risk of falling victim to online scams.
Overall, cybersecurity is a critical aspect of our digital lives, playing a vital role in protecting sensitive data, preserving online privacy, and maintaining the trust and security of individuals and businesses alike. Investing in cybersecurity measures is not just an option but a necessity in today’s interconnected world.
Cybersecurity Roles and Responsibilities
Within the realm of cybersecurity, professionals take on various roles and responsibilities to ensure the protection of sensitive information. Let’s explore cybersecurity professionals’ job descriptions and their different responsibilities in safeguarding digital assets.
Cybersecurity Job Description
- Cybersecurity Analyst: Responsible for monitoring network systems, identifying potential vulnerabilities, and implementing security measures to protect against cyber threats.
- Cybersecurity Engineer: Designs and develops security systems, including firewalls and intrusion detection systems, to safeguard digital infrastructures.
- Cybersecurity Consultant: Provides expert advice and guidance to organizations on developing and implementing cybersecurity strategies, policies, and procedures.
- Cybersecurity Incident Responder: Responds to and investigates security incidents, mitigating the impact and preventing future occurrences.
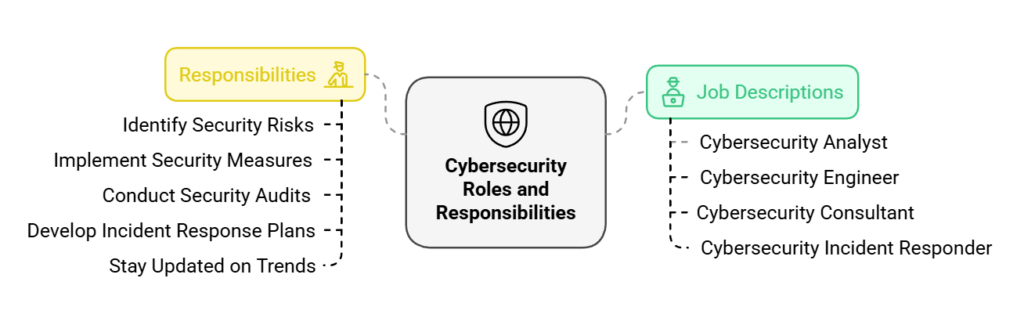
Cybersecurity Responsibilities
The responsibilities of cybersecurity professionals are wide-ranging and essential for maintaining a strong defense against cyber threats. Some of these responsibilities include:
- We identify and analyze potential security risks and vulnerabilities within an organization’s digital infrastructure.
- We are implementing security measures, such as firewall configurations, access controls, and encryption protocols, to protect sensitive data.
- We are conducting regular security audits and assessments to identify and address any weaknesses in the system.
- Developing and implementing incident response plans to handle and mitigate security incidents effectively.
- We keep updated with the latest cybersecurity trends, threats, and technologies to enhance security measures continuously.
Overall, cybersecurity professionals are responsible for ensuring the confidentiality, integrity, and availability of information in the face of evolving cyber threats. Their expertise and dedication are vital in maintaining the security posture of organizations in today’s digital landscape.
Cybersecurity Measures and Solutions
Protecting personal data in the digital age requires comprehensive cybersecurity protection measures. Cybersecurity professionals employ a variety of solutions to safeguard sensitive information from cyber threats. This section explores the technologies, tools, and best practices to ensure data confidentiality, integrity, and availability.
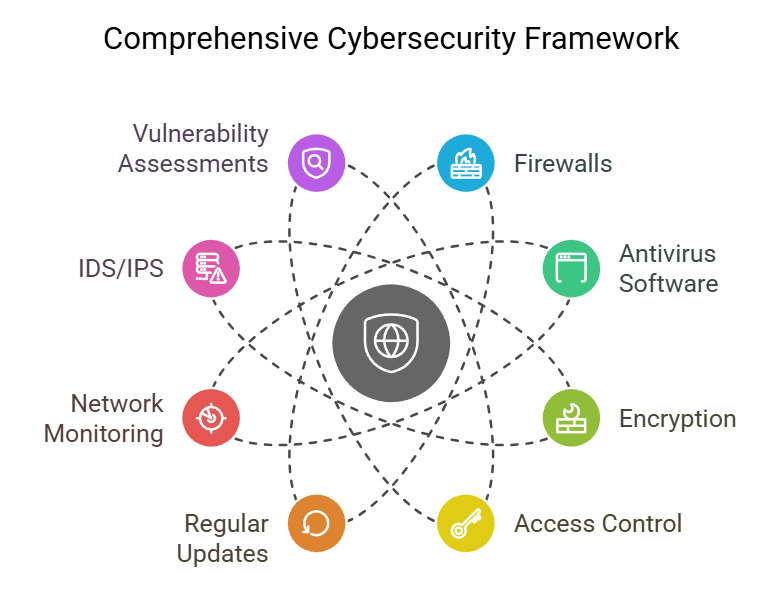
Cybersecurity Protection Measures
Cybersecurity protection measures are crucial in defending against various cyber threats. These measures include:
- Firewalls: Firewalls act as a barrier between internal networks and external sources, monitoring and controlling incoming and outgoing network traffic.
- Antivirus Software: Antivirus software scans systems for malware and viruses, preventing their execution and protecting against potential damages.
- Encryption: Encryption ensures that sensitive data is converted into a secure code, making it unreadable to unauthorized users.
- Access Control: Access control mechanisms regulate user permissions, limiting access to sensitive information based on role and need.
- Regular Updates and Patches: Keeping software, applications, and systems updated with the latest security patches is essential for addressing vulnerabilities.
Cybersecurity Solutions
Effective cybersecurity solutions go beyond just individual protection measures. They involve a holistic approach to safeguarding data and preventing cyber incidents. Some notable cybersecurity solutions include:
- Network Monitoring: Continuous network monitoring allows for real-time detection of suspicious activities, enabling prompt response to potential threats.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): IDS and IPS solutions identify and prevent unauthorized network access and attacks.
- Vulnerability Assessments: Regular vulnerability assessments uncover potential weaknesses in systems, allowing organizations to strengthen their security measures.
- Security Awareness Training: Educating individuals about potential cyber threats and best practices is key to building an organization’s security-conscious culture.
- Incident Response Planning: A well-defined incident response plan enables organizations to handle and mitigate the impact of cyber incidents effectively.
“Investing in robust cybersecurity measures and solutions is essential for protecting personal data and ensuring a safe digital environment. It’s not just about implementing individual protection measures; it’s about adopting a comprehensive approach to cybersecurity.”
Implementing cybersecurity technologies, tools, and best practices is crucial as organizations and individuals continue to face evolving cyber threats. Individuals and businesses can mitigate risks and maintain online security by staying proactive and prioritizing data protection.
Cybersecurity Benefits and Impact
Implementing effective cybersecurity measures has numerous benefits and significantly impacts individuals and organizations. By protecting sensitive information and preventing cyber threats, cybersecurity enhances trust, safeguards reputation, and contributes to a safe digital environment.
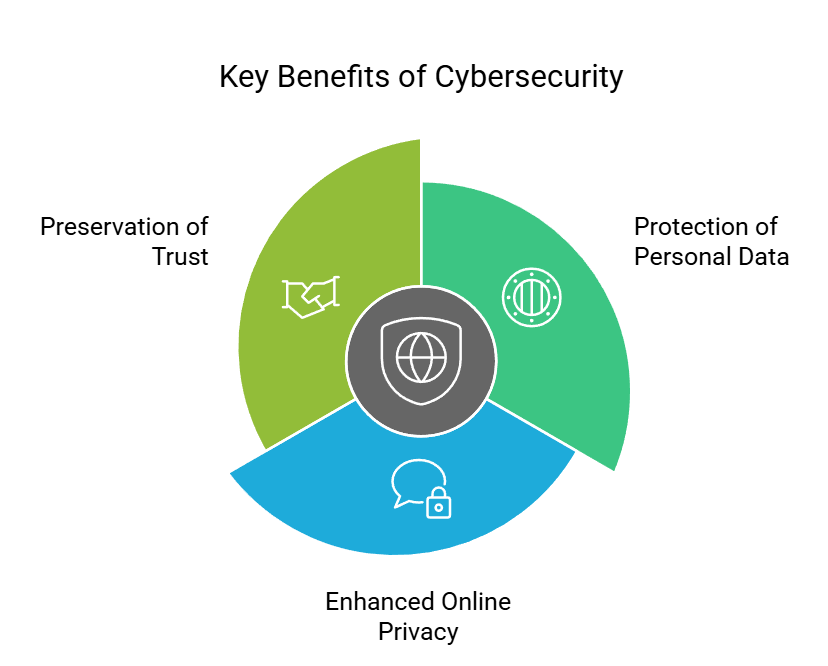
Benefits of Cybersecurity
- Protection of Personal Data: Cybersecurity measures ensure the safety and confidentiality of personal information, including financial data, login credentials, and personal records. This prevents unauthorized access and protects individuals from identity theft and financial fraud.
- Enhanced Online Privacy: By implementing cybersecurity protocols, individuals can enjoy more privacy while browsing the internet. Cybersecurity measures, such as encrypted communication and secure browsing practices, help protect personal data from being monitored or intercepted by malicious actors.
- Preservation of Trust: Strong cybersecurity measures foster trust between individuals, businesses, and online platforms. When users know their information is secure, they are more likely to engage in online transactions, share their data with trusted platforms, and have confidence in the digital ecosystem.
Read More: Why is Cyber Security Important?
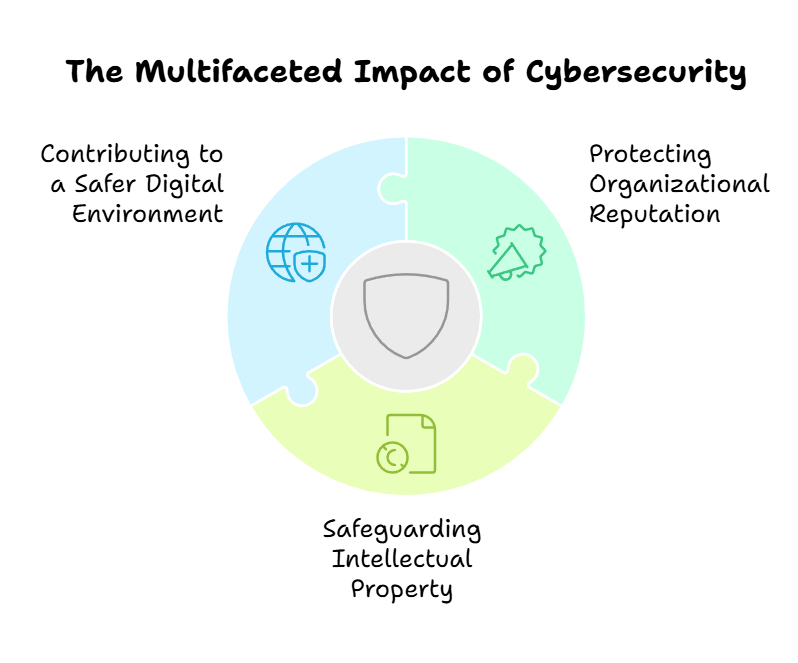
Cybersecurity Impact
- Protecting Organizational Reputation: Cybersecurity plays a crucial role in preserving an organization’s reputation. A data breach or cyber attack can have detrimental consequences, including damage to the brand’s image, loss of customer trust, and financial repercussions. Implementing robust cybersecurity measures mitigates these risks and safeguards the organization’s reputation.
- Safeguarding Intellectual Property: Cybersecurity protects valuable intellectual property, including patents, trade secrets, and proprietary information. Cybersecurity measures help organizations maintain their competitive edge and protect their innovations by preventing unauthorized access or theft of confidential data.
- Contributing to a Safer Digital Environment: Implementing cybersecurity measures contributes to a safer digital ecosystem for individuals and businesses. By preventing cyber attacks, cybersecurity professionals work towards minimizing the potential disruption caused by malicious actors and protecting critical infrastructure from cyber threats.
Investing in robust cybersecurity measures is a practical necessity and a strategic advantage for individuals and organizations, considering its significant impact on privacy, reputation, and overall security.
Cybersecurity Strategies and Objectives
Effective cybersecurity strategies are crucial in today’s digital landscape to ensure the protection and confidentiality of sensitive information. Companies must develop robust cybersecurity plans aligning with their specific needs and risk profiles.
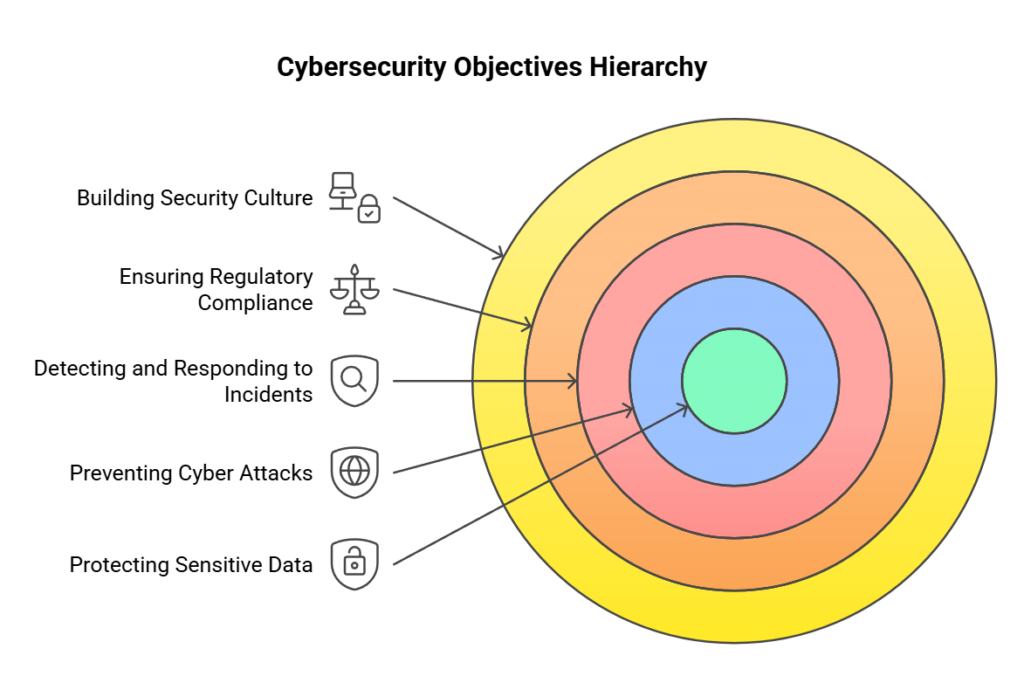
Defining Cybersecurity Objectives
Cybersecurity objectives outline the desired outcomes of a company’s cybersecurity efforts. These objectives may include:
- Protecting sensitive data from unauthorized access or disclosure
- Preventing cyber attacks and minimizing the risk of security breaches
- Detecting and responding to security incidents promptly
- Ensuring regulatory compliance with data protection laws and industry standards
- Building a strong security culture and raising cybersecurity awareness among employees
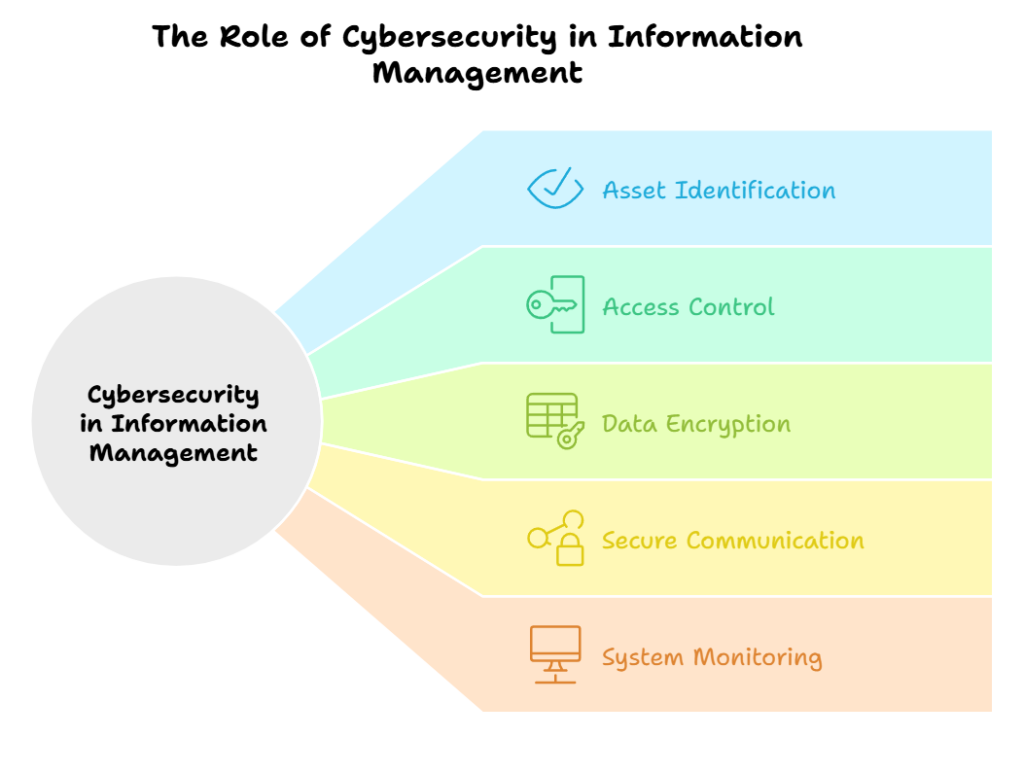
The Role of Cybersecurity in Information Management
Cybersecurity plays a critical role in effectively managing and protecting sensitive information. It involves:
- Identifying and prioritizing valuable assets and data that require protection
- Implementing appropriate access control measures to limit unauthorized access
- Encrypting data to maintain its confidentiality and integrity
- Establishing secure communication channels to protect information during transmission
- Regularly monitoring and auditing systems to identify and address vulnerabilities
Effective cybersecurity strategies safeguard against potential threats and enable businesses to operate with confidence and trust while leveraging the benefits of digital technologies.
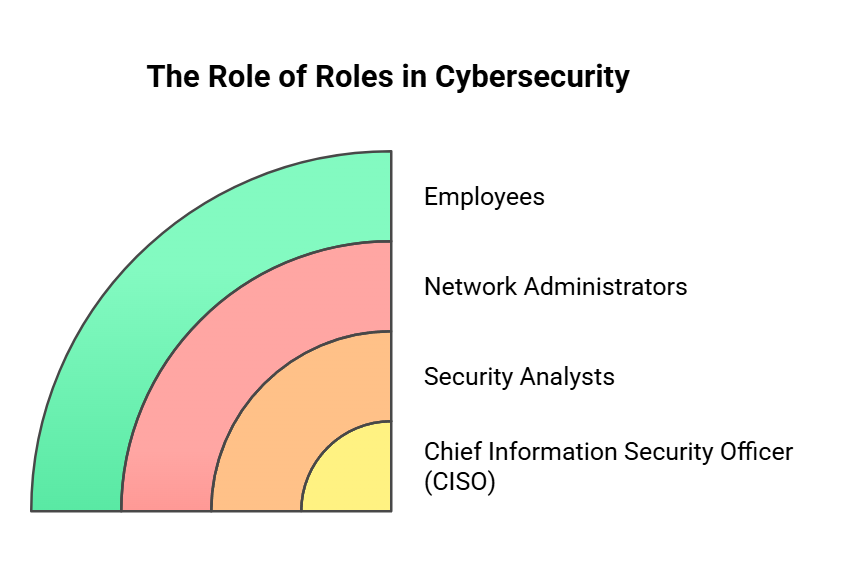
The Role of Roles in Cybersecurity
Successful cybersecurity implementation involves assigning clear roles and responsibilities to various stakeholders. Some common roles in cybersecurity include:
- Chief Information Security Officer (CISO): Responsible for developing and implementing the organization’s cybersecurity strategy
- Security Analysts: Analyze and assess security risks, implement security measures, and monitor systems for potential threats.
- Network Administrators: Manage network infrastructure and ensure its security and resilience
- Employees: Follow security protocols, practice good cyber hygiene, and report any suspicious activities
Organizations can ensure that cybersecurity measures are implemented effectively and consistently across all levels by defining roles and establishing clear responsibilities.
Read More: What is the Main Role of Cyber Security?
Cybersecurity Awareness and Education
Developing awareness and educating individuals about cybersecurity is imperative in today’s digital landscape. With cyber threats becoming more sophisticated, everyone must have a solid understanding of cybersecurity and the steps they can take to protect themselves and their sensitive information.
The Significance of Cybersecurity Awareness Programs
Cybersecurity awareness programs play a vital role in educating individuals about the potential risks and threats they may encounter online. These programs aim to raise awareness about common cyber attacks, such as phishing scams, malware infections, and identity theft, and guide how to detect and prevent them.
Individuals gain insights into the ever-evolving cyber threat landscape by participating in cybersecurity awareness programs. They learn about the different attack vectors used by cybercriminals and understand how to identify and respond to suspicious activities. This knowledge empowers them to stay vigilant and proactively safeguard their personal information.
The Importance of Educating Users
Education is a key component of cybersecurity. Users must be educated about the potential risks they face when using digital technologies and taught how to mitigate them effectively. Without proper education, individuals may unknowingly engage in unsafe online practices that can compromise their sensitive data.
Understanding cybersecurity helps individuals protect themselves and contributes to a safer digital environment overall. When users are well-informed about potential threats and cybersecurity best practices, they can actively contribute to the collective defense against cyber attacks, making it harder for cybercriminals to succeed.
Tips for Staying Safe Online
Here are some practical tips that individuals can follow to enhance their cybersecurity:
- Use strong and unique passwords for all online accounts.
- Enable multi-factor authentication for added security.
- Keep software and operating systems up to date with the latest security patches.
- Be cautious of suspicious emails, attachments, and links.
- Regularly back up important data to protect against data loss.
- Use reputable antivirus software and keep it updated.
- Avoid sharing personal information on unsecured websites or with untrusted sources.
By following these tips, individuals can significantly reduce their risk of falling victim to cyber-attacks and protect their personal information from unauthorized access.
Remember, cybersecurity awareness and education are ongoing processes. It is essential to stay informed about emerging threats and evolving best practices to ensure the highest level of protection in an ever-changing digital landscape.
Cybersecurity Services and Solutions
When protecting sensitive data and defending against cyber threats, organizations often turn to cybersecurity service providers for expert assistance. These professionals offer services designed to enhance security measures and safeguard valuable information. Whether it’s vulnerability assessments, incident response, or security consulting, cybersecurity services are crucial in maintaining a robust defense system.
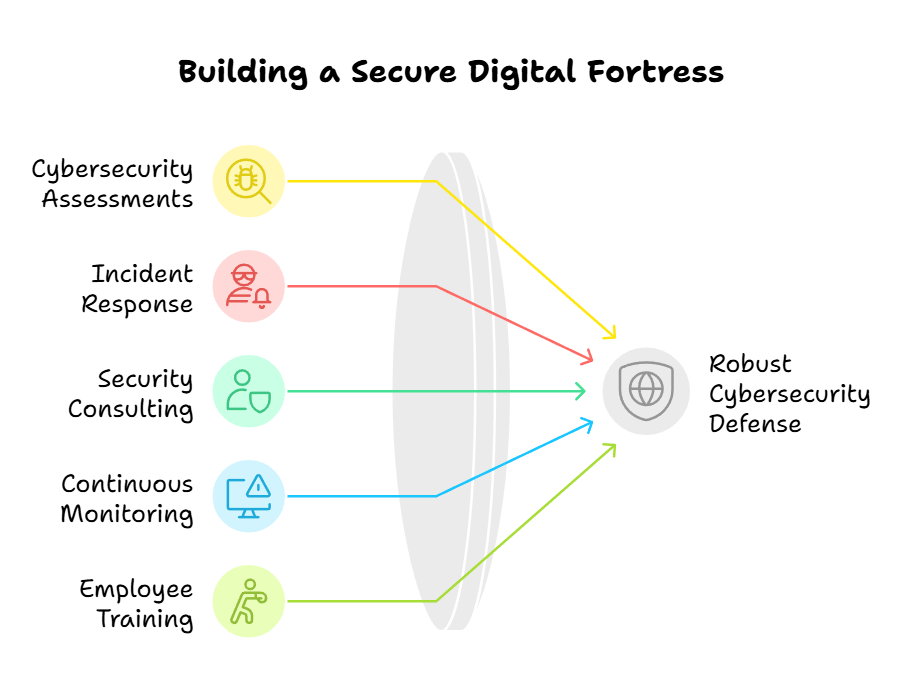
The Key Components of a Robust Cybersecurity Defense System
Organizations need a comprehensive defense system to defend against cyber attacks and protect valuable data effectively. Here are some essential components:
- Cybersecurity Assessments: Cybersecurity professionals conduct thorough assessments to identify vulnerabilities and potential risks. This helps organizations understand their current security posture and implement appropriate protection measures.
- Incident Response: In the event of a cyber-attack or breach, incident response teams are ready to take immediate action. They investigate the incident, contain the damage, and ensure it is properly documented for future prevention.
- Security Consulting: Cybersecurity experts provide valuable advice and guidance on security strategies, policies, and best practices. They help organizations develop robust security frameworks that align with industry standards and regulatory requirements.
- Continuous Monitoring: Monitoring systems and technologies detect and respond to potential threats in real time. This allows organizations to address vulnerabilities and prevent unauthorized access or data loss proactively.
- Employee Training: A well-informed and security-aware workforce is a critical defense against cyber threats. Cybersecurity service providers offer training programs to educate employees on best practices, safe browsing habits, and maintaining strong passwords.
Partnering with a trusted cybersecurity service provider like Ark Solvers can provide peace of mind, knowing that your organization’s security needs are in capable hands. With their comprehensive range of services and expert guidance, you can confidently navigate the complex landscape of cyber threats and ensure the protection of your valuable data.
Conclusion: what does cybersecurity do
In conclusion, cybersecurity is of utmost importance in today’s digital landscape. With the increasing number of online threats and potential risks to personal data, implementing robust cybersecurity measures is crucial to ensure the safety and confidentiality of sensitive information. Whether protecting individuals or organizations, cybersecurity is a vital defense against cyber attacks.
By staying updated on the latest cybersecurity practices and continuously assessing and improving security protocols, individuals and organizations can effectively adapt to the ever-evolving threats in the digital world. Ark Solvers, a leading cybersecurity company, provides comprehensive solutions to safeguard personal data from potential online dangers.
Remember, cybersecurity isn’t a one-time effort but an ongoing process that requires constant vigilance. Investing in cybersecurity tools, technologies, and solutions that protect against data breaches, unauthorized access, and other cyber threats is essential. Individuals and organizations can confidently navigate the digital landscape and safeguard sensitive information with the right security measures.
What does Cybersecurity Do – FAQ
What is cybersecurity?
Cybersecurity refers to the practices, technologies, and measures to protect digital systems, networks, and data from cyber threats and unauthorized access. It encompasses various strategies to ensure the confidentiality, integrity, and availability of information, safeguarding against potential risks and vulnerabilities.
Why is cybersecurity important?
Cybersecurity is vital in today’s digital landscape due to the increasing presence of cyber threats and the potential damage they can cause. It safeguards personal and sensitive data, prevents unauthorized access to systems, and protects individuals and organizations from financial losses and reputational damage. It is essential to maintain trust, privacy, and security online.
What are the functions of cybersecurity?
The primary function of cybersecurity is to protect digital systems, networks, and data from unauthorized access, manipulation, and damage. It involves risk assessment, vulnerability management, incident response, and implementing security controls and measures. Cybersecurity professionals also conduct security assessments, develop security policies, and educate users about potential threats.
What are some common cybersecurity measures and solutions?
Common cybersecurity measures and solutions include firewalls, antivirus software, encryption, multi-factor authentication, intrusion detection and prevention systems, regular software updates, backup and recovery strategies, and employee training and awareness programs. These measures protect against various cyber threats, such as malware, phishing attacks, data breaches, and unauthorized access.
What are the roles and responsibilities in cybersecurity?
The roles and responsibilities in cybersecurity vary depending on the organization and the specific job positions. However, common roles include cybersecurity analysts, engineers, incident responders, ethical hackers, and security consultants. These professionals are responsible for monitoring systems for security breaches, investigating and resolving security incidents, implementing security controls, and ensuring compliance with security policies and regulations.
What are the benefits and impacts of cybersecurity?
Implementing cybersecurity measures provides several benefits, such as protecting personal and sensitive data, preventing financial losses, maintaining trust and reputation, adhering to regulatory requirements, and reducing business disruption. It also has a broader impact by contributing to a safer digital environment, deterring cybercriminals, and promoting innovation and growth in the digital economy.
What are some common cybersecurity strategies and objectives?
Common cybersecurity strategies include:
- Creating a comprehensive security framework.
- Conducting regular risk assessments.
- Implementing security controls based on industry best practices.
- Continually monitoring and improving security measures.
Objectives include:
- Preventing data breaches.
- Mitigating risks.
- Ensuring regulatory compliance.
- Detecting and responding to security incidents.
- Educating employees and users about cybersecurity best practices.
How can individuals enhance cybersecurity awareness?
Individuals can enhance cybersecurity awareness by staying informed about the latest threats and vulnerabilities, practicing good password hygiene, being cautious of suspicious emails and links, keeping software and systems updated, using secure Wi-Fi networks, and regularly backing up important data. Education and training programs, such as cybersecurity awareness campaigns and workshops, can also significantly raise awareness and promote responsible online behavior.
What are the services provided by cybersecurity professionals?
Cybersecurity professionals offer various services, including vulnerability assessments, penetration testing, network security monitoring, incident response and recovery, security consulting, and security awareness training. These services help organizations identify and address. Companies must identify vulnerabilities, respond to and recover from security incidents, and develop tailored security strategies to mitigate risks.




