What Is Hashing in Cyber Security? A Comprehensive Guide
Have you ever wondered how organizations protect their data? How do they make sure info is safe when it moves around? The big secret is hashing. But What is Hashing in Cyber Security, and why is it so important for keeping secrets safe?
This guide is going to teach you all about hashing in cyber security. We’ll cover the basics and explain why it’s key to keeping data and info safe. You’ll understand why hashing is a big deal for staying secure in the digital world.

Key Takeaways:
- Hashing is a powerful technique that plays a vital role in ensuring data integrity and secure information transfer in cyber security.
- Hashing utilizes cryptographic hash functions to generate unique hash values that verify data authenticity and protect against tampering.
- Understanding and implementing hashing techniques can greatly enhance organizations’ overall security measures in safeguarding sensitive information.
- Hashing is widely used in password storage, data authentication, secure communication, and blockchain technology.
- By exploring this comprehensive guide, you will gain valuable insights into the world of hashing and its crucial role in cyber security.
Understanding Hashing Algorithms in Cyber Security
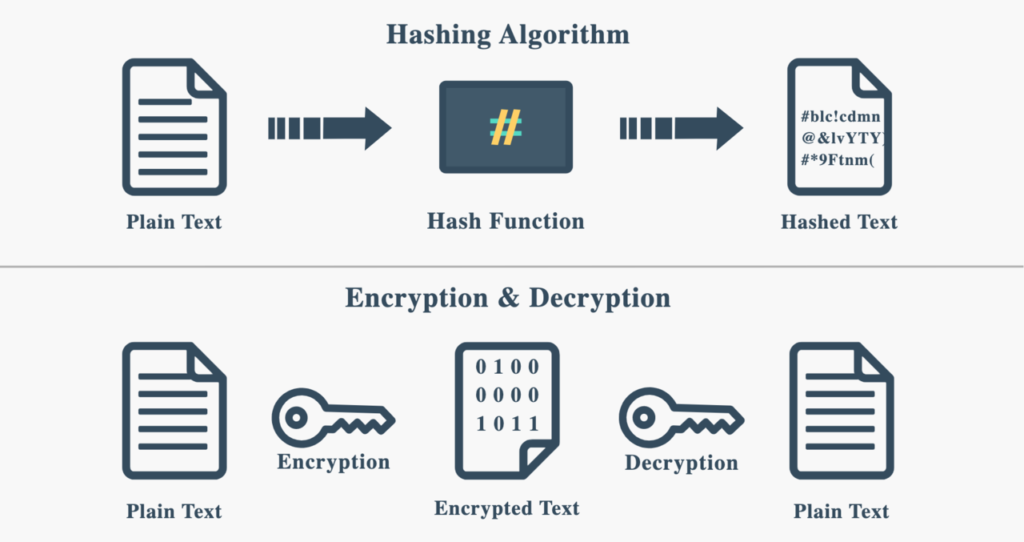
In the world, hashing algorithms are key for keeping data safe. They use encryption to hide information and make sure it stays private and unchanged. These algorithms turn data into unique codes called hash values. A special function, the hash function, does this task.
The hash function is a complex math trick. It takes in data and turns it into a string of characters that cannot be turned back. Cryptographers use hash functions to transmit and store data securely.
There are many types of hash functions, each with its pluses and minuses. For important tasks, we use strong cryptographic algorithms, like MD5 and SHA-256. These are meant to keep data safe by making it nearly impossible for two different pieces of data to have the same hash value.
Hashing is vital in data encryption too. It transforms data in a way that only the right key can change back. This makes sure that if someone is not allowed to try to look at the data, they can’t understand it without that special key.
Hash values also help ensure data hasn’t been tampered with. By comparing hash values of data before and after sending it, a company can check if it’s the same. If the hash values match, the data is safe. If they don’t, something went wrong.
Here’s an example to help you see how all this works:
Maintaining Data Integrity: An Example
Let’s say Company X needs to send secret info to Company Y. Company X puts the data through a hashing algorithm for safety. Then, they join the hash value with the encrypted data.
Company Y, upon getting this data, does the same procedure. It calculates a hash value for the received data. If the new hash value matches the one from Company X, the data is secure.
If the hash values aren’t the same, the data possibly got changed. This situation needs serious checking to confirm if the info is still accurate.
Learning about and using hashing algorithms is vital for protecting data. By choosing well-known security methods and regularly checking hash values, organizations can greatly improve their data protection. This stops unknown people from getting to the important data.
Importance of Hashing for Data Security
Hashing is key to keeping our data secure. It’s a core part of cyber security, ensuring our information is safe. By encrypting our data, it verifies and keeps it private.
Hashing helps check if data is real. It turns our data into unique codes for verification. If the data changes, so does the hash value, which warns of tampering.
It’s also vital for safe messaging. Hashing helps make sure messages or files aren’t changed. This way, talking online is more secure.
Another use is to protect sensitive info like passwords. Hashing turns this info into unreadable data. Even if someone guesses the code, they can’t see the original info.
Read More: Different Types of Cyber Security
Secure Authentication and Data Verification
Hashing is great for security checks, too. It helps quickly see if two pieces of data are the same. This is especially useful for big amounts of data.
Hashing does a lot for our data’s safety. It’s key for checking data, keeping messages secure, and protecting our private info. Using hashing, companies can better defend against cyber attacks.

Hashing Techniques in Cyber Security
Hashing techniques are crucial in cyber security. They help keep sensitive data safe and maintain its integrity. We will look into how these techniques are used practically. Plus, we’ll see their role in protecting digital information.
1. Password Hashing and Secure Password Storage
Secure passwords are key to keeping user accounts safe. Organizations use cryptographic hash functions for this. They can safely store passwords. This protects users from hacks and unauthorized access. Though hash collisions are possible, secure methods reduce this risk.
2. Secure Data Storage
Keeping data secure is vital in cyber security. Hashing creates unique digital fingerprints for data. These fingerprints, or hash values, ensure data integrity. They catch any unauthorized changes. Hashing methods like MD5 and SHA-256 are popular for this.
3. Secure Hashing Methods
Secure hashing uses advanced cryptographic functions. They prevent data from being easily reversed or tampered with. MD5 and SHA-256 are well-known in the field. While MD5 has some security risks, SHA-256 is more secure. This greater security comes from its size and strong cryptographic features.
Now, let’s look at a table to compare MD5 and SHA-256:
| Algorithm | Hash Size | Strength | Common Usage |
|---|---|---|---|
| MD5 | 128 bits | Weaker | Legacy systems, non-critical applications |
| SHA-256 | 256 bits | Stronger | Enterprise systems, critical applications |
The table shows that MD5 is weaker and fits best for old systems or simple needs. On the flip side, SHA-256 is stronger and ideal for bigger, more critical systems.
To protect data in cyber security, using secure hashing techniques is a must. Passwords should be hashed, data stored securely, and the right algorithms chosen. This helps keep digital information safe and sound.
Applying Hashing in Cyber Security Best Practices
Cybersecurity relies heavily on using cybersecurity algorithms like hashing. Hashing is great for keeping important info safe. It makes sure only the right people can access the data.
Hashing is key in many security steps, especially for keeping data safe in blockchain technology and using cryptographic algorithms. In blockchain, it helps make sure data can’t be changed. Cryptographic methods use hashing to keep any sharing or saving of data secure.
Implementing Hashing in Cyber Security Measures
To use hashing well, companies need to follow some top tips:
- Data Encryption: Hashing is good for hiding secret info, and making sure it stays safe when stored or shared.
- Password Hashing: It lets companies keep users’ login details safe from the wrong hands by changing them into a safer form.
- Secure Data Storage: Hashing helps check if data’s been changed, stopping anyone from sneaking in and messing with it.
- Data Authentication: It also keeps info real and safe for companies to use, so they know it’s trusted.
With these cyber security best practices in place, companies can make their digital forts stronger. They protect their precious data from the dangers online.
The Role of Collision Resistance
Collision resistance is super important in hashing. It means it’s very hard for someone to sneak in similar info and mess things up. This keeps the bad guys from tricking the system.
Choosing well-protected hashing systems is a must. That’s why experts prefer hash types like MD5 and SHA-256. These are known for being very hard to break.
Using hashing correctly is vital for ensuring data safety online. With strong cyber security measures, and the right use of cyber security algorithms, like hashing, companies can keep their info safe from cyber attacks.
| Benefits of Applying Hashing in Cyber Security |
|---|
| Enhanced data security and protection |
| Secure storage of sensitive information |
| Authentication and verification of data integrity |
| Protection against unauthorized access |
| Effective encryption of sensitive data |
Conclusion
This comprehensive guide explored hashing in cyber security. We looked at the basics, why they’re vital for data security, types of hashing, and their uses in cyber security practices.
Understanding hashing helps organizations boost their security. It keeps important info safe from people who shouldn’t see it.
Strong hashing algorithms protect data from being changed by the wrong people. Plus, they make sure info stays private and intact when it’s shared. With tech always improving and threats growing, staying alert and using the advice in this guide is key to avoiding cyber-attacks.
FAQ
What is hashing in cyber security?
Hashing in cyber security turns data into a fixed-length string, called a hash value, with a cryptographic hash function. It’s vital to protect data by verifying its integrity. This process helps spot any changes or tampering.
How do hashing algorithms contribute to data encryption?
Hashing algorithms in encryption protect data’s confidentiality and integrity. They turn input data into a unique hash value. This makes it very hard to find the original data from the hash. Thus, it secures data from being read by unauthorized people.
What are the different types of hash functions used in cyber security?
In cyber security, we use hash functions like MD5, SHA-1, and SHA-256. These offer different security levels by producing hash values of various lengths. For example, SHA-256 is harder to break than MD5 or SHA-1.
How does hashing ensure data authentication and protection?
Hashing is key for authenticating and protecting data. By comparing the hash of the received data with the original, you can verify its integrity. It also secures data transfer and storage. Any changed data will show a different hash, warning of tampering.
How does hashing contribute to secure communication and authentication?
Hashing makes communication and authentication safer through MACs. MACs use a secret key and a hashed message to create a unique code. This code confirms a message’s authenticity and deters tampering.
What are some secure hashing methods used in cyber security?
Secure hashing in cyber security includes password hashing and secure password storage. These methods make it hard to uncover passwords from their hash values. MD5 and SHA-256 are popular for securing data and checking its integrity.
How does hashing contribute to cyber security best practices?
Hashing is at the core of cyber security strategies. It checks the accuracy of data, safeguards crucial information, and blocks unauthorized data access. In blockchain, it preserves transaction integrity. Preventing duplicate hash values is crucial in these cryptographic methods.






