Exploring the Top 10 Types of Cyber Security Threats

Exploring the Various Types of Cyber Security Threats 2025
Types of Cyber Security Threats: As technology advances at an astonishing pace, the threat landscape in the digital world is constantly evolving. Cyber security has become a critical concern for individuals and businesses as cybercriminals deploy increasingly sophisticated tactics to exploit vulnerabilities and wreak havoc.
But have you ever wondered what types of cyber security threats are most prevalent in 2025?
This article will deeply dive into cyber security threats, examining the wide range of dangers in today’s digital age. From familiar cyber attacks to emerging threats, we will provide you with a comprehensive list of the most common and impactful cyber threats that individuals and organizations need to be aware of.
So, are you ready to explore the dangers lurking in cyberspace and uncover the secrets behind these nefarious activities?
Read More: Different Types of Cyber Security
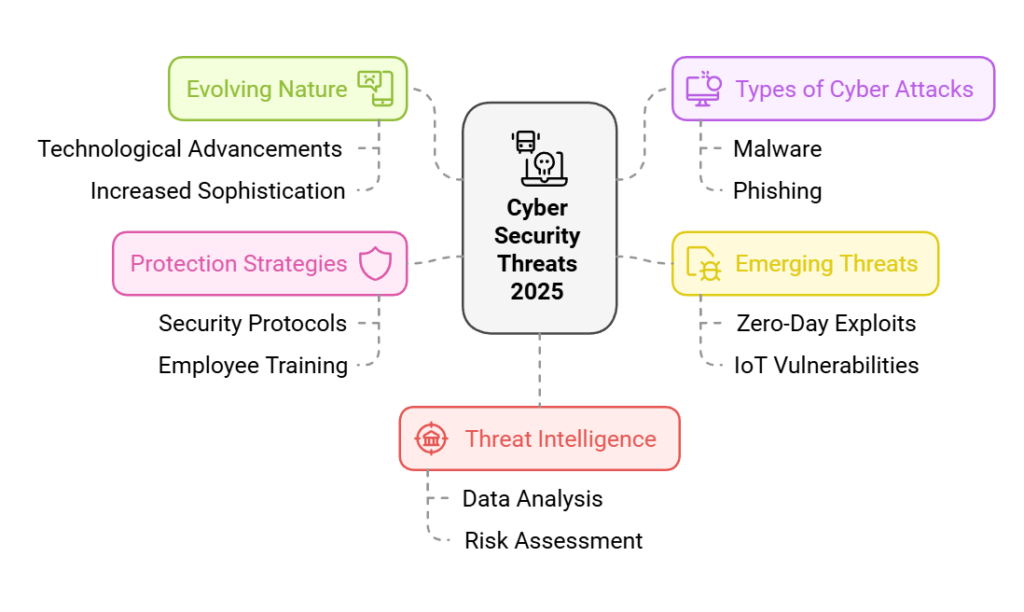
Key Takeaways:
- Understand the evolving nature of cyber security threats in 2025.
- Explore the various types of cyber attacks and their implications.
- Identify emerging cyber threats and vulnerabilities.
- Learn how to protect yourself and your organization against cyber threats.
- Gain insights into the role of cyber threat intelligence in mitigating risks.
Understanding the Landscape of Cyber Security Threats
In today’s digital age, cyber threats are a prevalent concern for individuals and organizations. Understanding the cyber threat landscape is crucial for implementing effective security measures. This section will delve into the most common cyber security threats and explore their various attack types. We will also categorize these threats, providing a comprehensive list of cyber threats organizations must prepare for.
The Most Common Cyber Security Threats
Cyber threats come in various forms, each targeting different aspects of online security. By familiarizing ourselves with the most common cyber security threats, we can better protect our systems and data. Here are some of the leading cyber threats:
Read More: What are the 4 types of cyber threats?
- Malware: Malicious software, such as viruses, worms, and ransomware, can infect systems and cause damage or extract sensitive information.
Read More: What is Malware? Malware Definition, Types, and Protection
- Phishing: Cybercriminals use deceptive tactics to trick individuals into revealing confidential information, usually through fraudulent emails or websites.
Read More: What Is Phishing? – Definition, Types of Attacks, Examples
- Denial of Service (DoS) attacks: overwhelm network resources, rendering systems and services unavailable to legitimate users.
Read More: What is a Denial of Service (DoS) attacks? types, Examples
- Man-in-the-Middle (MitM) Attacks: Cybercriminals intercept and manipulate communication between two parties, gaining unauthorized access to sensitive information.
Read More: What Is a Man-in-the-Middle Attack (MitM)?
- SQL Injection: By exploiting vulnerabilities in web applications, attackers can inject malicious SQL code, compromising and manipulating databases.
Read More: What is SQL Injection (SQLi) and How to Prevent Attacks
- Advanced Persistent Threats (APTs): These long-term, highly sophisticated attacks aim to gain unauthorized access to systems, usually for espionage or data theft purposes.
Read More: What Is an Advanced Persistent Threat (APT)?
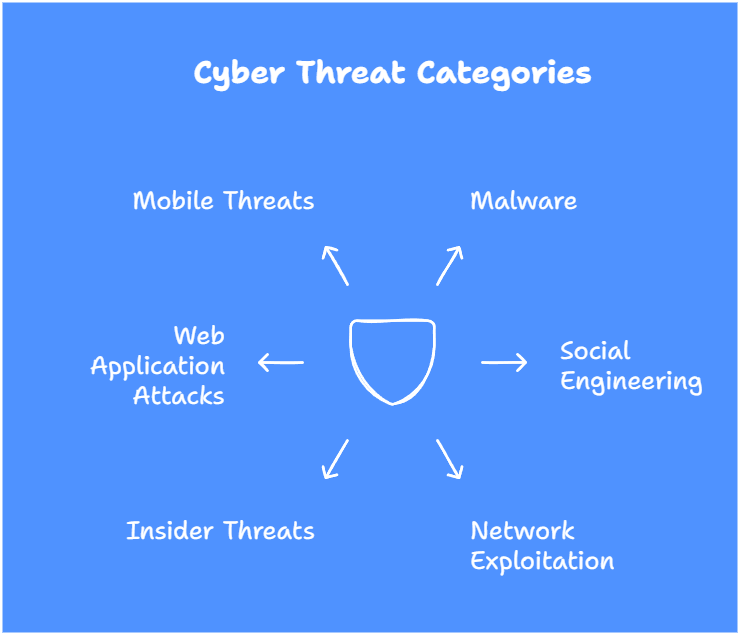
Categories of Cyber Threats
In addition to understanding the common cyber threats, it is essential to categorize them based on their nature and impact. Here are the primary categories of cyber threats:
| Category | Description |
| Malware | Malicious software is designed to disrupt systems, steal data, or gain unauthorized access. |
| Social Engineering | Manipulating human behavior to deceive and trick individuals into revealing sensitive information. |
| Network Exploitation | Exploiting vulnerabilities in network infrastructure or protocols to gain unauthorized access or disrupt services. |
| Insider Threats | Threats posed by authorized individuals within an organization, intentionally or unintentionally compromising security. |
| Web Application Attacks | Targeting vulnerabilities in web applications to gain unauthorized access, manipulate data, or disrupt services. |
| Mobile Threats | Threats targeting mobile devices, applications, or networks, compromising data, or breaching privacy. |
By understanding the different categories, organizations can prioritize their security efforts and allocate resources accordingly, ensuring comprehensive protection against cyber threats.
Read More: What Is a Web Application Attack?
Emerging and Evolving Cyber Security Threats
As technology advances, so do the cyber security threats that organizations face. Staying informed about the latest trends and emerging threats is crucial for maintaining a strong defense against cyber attacks. This section will explore the ever-evolving landscape of cyber security threats and provide insights into the top threats that organizations should be prepared for.
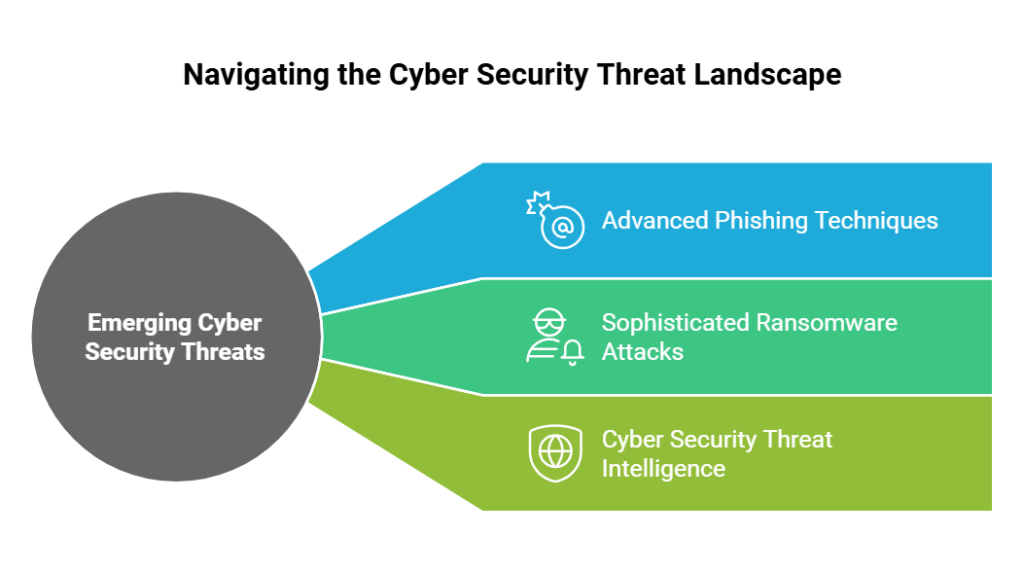
The Threat Intelligence Advantage:
Effective cyber security strategies rely on timely and accurate information about potential threats. Cyber security threat intelligence plays a crucial role in identifying emerging cyber threats and vulnerabilities. By gathering data from various sources and analyzing it, organizations can gain valuable insights into the tactics used by cyber criminals and take proactive measures to protect their systems and data.
Emerging Cyber Threats:
The digital landscape constantly evolves, creating new cyber security threats. Cybercriminals continuously find innovative ways to exploit vulnerabilities, from advanced phishing techniques to sophisticated ransomware attacks. Understanding these emerging threats is essential for staying one step ahead of cyber criminals and implementing effective safeguards.
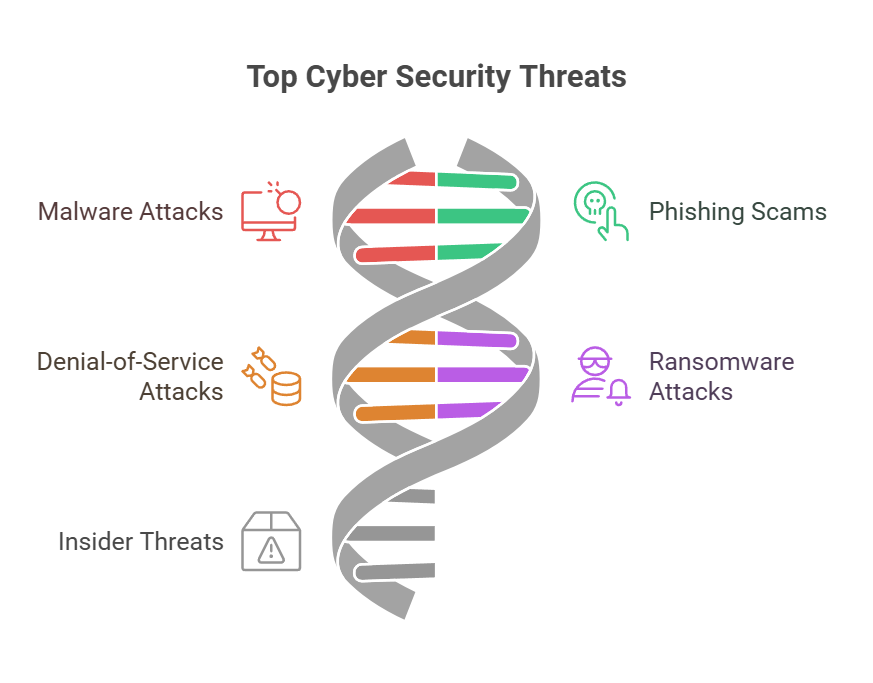
Top Cyber Security Threats:
While the cyber threat landscape is vast and ever-changing, some threats consistently rank among the top regarding severity and impact. These major cyber security threats include:
- Malware Attacks
- Phishing Scams
- Denial-of-Service (DoS) Attacks
- Ransomware Attacks
- Insider Threats
Read More: What is an Insider Threat? Definition, Types, & Examples
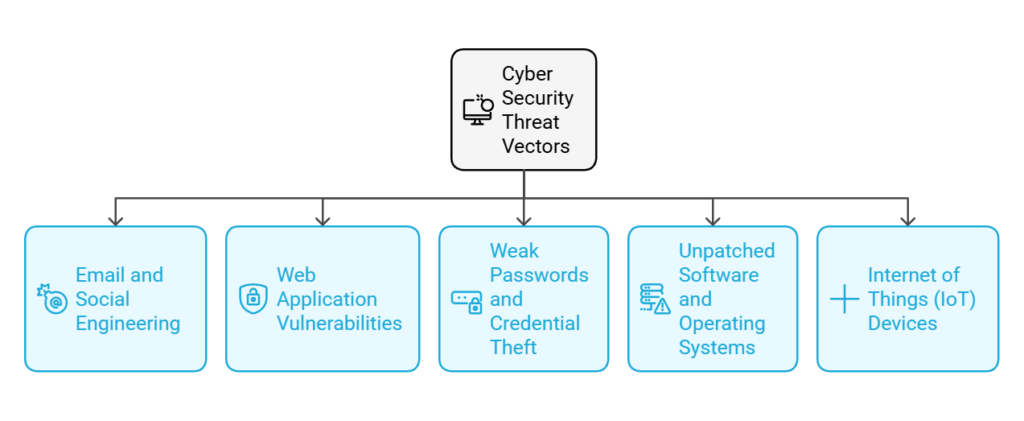
Cyber Security Threat Vectors:
Cyber attackers exploit various vectors for malicious activities. Understanding these vectors is crucial for implementing effective security measures. Some common cyber security threat vectors include:
- Email and Social Engineering
- Web Application Vulnerabilities
- Weak Passwords and Credential Theft
- Unpatched Software and Operating Systems
- Internet of Things (IoT) Devices
Read More: What is Internet of Things Security? and Why It’s Important
By understanding these emerging cyber threats and the vectors used by cybercriminals, organizations can better prioritize their security measures and allocate resources accordingly. It is crucial to stay updated on the latest cyber security threat landscape and continuously evolve defenses to protect against the ever-changing cyber threat landscape.
| Cyber Security Threat | Description | Prevention Techniques |
| Malware Attacks | Malicious software is designed to disrupt systems, steal data, or gain unauthorized access. | Regularly update software, use antivirus software, practice safe browsing habits, and educate employees on phishing scams. |
| Phishing Scams | Fraudulent techniques trick individuals into revealing sensitive information, such as passwords or credit card details. | Implement email filters, educate employees about phishing techniques, and use multi-factor authentication. |
| Denial-of-Service (DoS) Attacks | It was overwhelming a system or network with traffic to make it unavailable to legitimate users. | Implement strong network security measures, use traffic filtering, and consider using cloud-based DDoS protection services. |
| Ransomware Attacks | Malware that encrypts files and demands ransom in exchange for the decryption key. | Regularly back up data, keep systems and software updated, use antivirus software, and educate employees on safe online practices. |
| Insider Threats | Malicious or negligent behavior by an organization’s internal stakeholders that compromises security. | Implement access controls, monitor user activity, and provide regular cybersecurity training to employees. |
Read More: What Is Ransomware? – Definition, Prevention & More
Conclusion: Types of Cyber Security Threats
Throughout this article, we have explored the various types of cyber security threats that individuals and businesses face in 2025. From common cyber threats to emerging ones, it is clear that the cybersecurity landscape is constantly evolving.
It is crucial to stay vigilant against the latest cyber threats and understand the risk factors associated with online security. Cyber threat actors are becoming increasingly sophisticated, posing significant cyber security risks to organizations of all sizes.
Proactive measures are necessary to mitigate these risks. Investing in cyber threat intelligence and keeping up with the latest trends can help identify and prevent data breach incidents. We can protect ourselves and our businesses from the ever-evolving cyber threat landscape by staying informed and implementing robust security measures.
At Ark Solvers, we recognize the importance of cybersecurity and offer comprehensive solutions to safeguard your digital assets. Our expertise in cyber threat intelligence and risk assessment can help you stay one step ahead of cybercriminals. Don’t let your guard down – protect what matters most with Ark Solvers.
FAQ – Types of Cyber Security Threats
What are the different types of cyber security threats?
Cyber security threats include malware, phishing, ransomware, DDoS attacks, social engineering, and insider threats.
What are some common cyber threats that individuals and businesses face?
Some common cyber threats include email scams, identity theft, password attacks, network vulnerabilities, and unauthorized access to sensitive information.
What are the top cybersecurity threats in 2025?
The top cybersecurity threats in 2025 include AI-powered attacks, cryptojacking, IoT vulnerabilities, cloud security risks, and supply chain attacks.
How do cyber attacks exploit network security threats?
Cyber attacks exploit network security threats by targeting weaknesses in firewalls, routers, and other network devices to gain unauthorized access, disrupt services, or steal sensitive data.
What are the emerging cyber threats that organizations should be aware of?
Emerging cyber threats include deepfake technology, 5G-related vulnerabilities, data poisoning, quantum computing threats, and attacks targeting cloud-native technologies.
What are the major cyber security threats affecting businesses today?
Major cyber security threats affecting businesses today include data breaches, ransomware attacks, advanced persistent threats (APTs), supply chain attacks, and zero-day exploits.
How can organizations protect themselves against cyber threats?
Organizations can protect themselves against cyber threats by implementing robust security measures such as using strong passwords, regularly updating software and security patches, conducting employee training, and implementing multi-factor authentication.
What role does cyber threat intelligence play in preventing data breaches?
Cyber threat intelligence helps organizations proactively identify, detect, and mitigate potential cyber threats by providing valuable insights into threat actors’ tactics, techniques, and procedures.


